- Home
- LPI Certifications
- 300-100 LPIC-3 Exam 300: Mixed Environments Dumps
Pass LPI 300-100 Exam in First Attempt Guaranteed!
Get 100% Latest Exam Questions, Accurate & Verified Answers to Pass the Actual Exam!
30 Days Free Updates, Instant Download!


300-100 Premium File
- Premium File 60 Questions & Answers. Last Update: Jan 24, 2026
Whats Included:
- Latest Questions
- 100% Accurate Answers
- Fast Exam Updates
Last Week Results!
All LPI 300-100 certification exam dumps, study guide, training courses are Prepared by industry experts. PrepAway's ETE files povide the 300-100 LPIC-3 Exam 300: Mixed Environments practice test questions and answers & exam dumps, study guide and training courses help you study and pass hassle-free!
Complete Guide to LPIC-3 Mixed Environment Certification (300-100)
The LPIC-3 certification represents the pinnacle of achievement within the Linux Professional Institute's comprehensive certification framework. This advanced credential is meticulously designed for enterprise-level Linux professionals who demonstrate exceptional expertise in managing complex, heterogeneous computing environments. The Mixed Environment specialty, designated by exam code 300-100, focuses specifically on the intricate administration of Linux systems within diverse organizational infrastructures where multiple operating systems coexist harmoniously.
This certification pathway acknowledges the evolving nature of modern enterprise environments, where organizations frequently deploy hybrid architectures combining Linux distributions with Windows-based systems, proprietary platforms, and various authentication mechanisms. The LPIC-3 Mixed Environment certification validates a professional's capability to navigate these multifaceted technological landscapes while maintaining security, performance, and operational efficiency across disparate systems.
Candidates pursuing this certification must demonstrate comprehensive understanding of directory services, authentication protocols, file sharing mechanisms, and integration methodologies that enable seamless operation across different platforms. The examination encompasses critical areas including OpenLDAP administration, Samba configuration, Active Directory integration, and client management strategies that are essential for enterprise-level system administrators.
The certification process involves a rigorous 90-minute examination containing 60 carefully crafted questions that assess both theoretical knowledge and practical application skills. Candidates must achieve a minimum score of 500 out of 800 points to successfully obtain this prestigious credential, which represents the highest level of professional, distribution-neutral Linux certification available in the industry today.
OpenLDAP Configuration and Management Foundation
OpenLDAP replication constitutes a fundamental component of enterprise directory services, providing redundancy, load distribution, and fault tolerance across distributed environments. Understanding replication mechanisms is crucial for maintaining high availability and ensuring consistent directory information across multiple server instances within complex organizational infrastructures.
The replication architecture encompasses various methodologies including master-slave configurations, multi-master deployments, and sophisticated synchronization protocols that maintain data consistency across geographically distributed locations. Master servers function as authoritative sources for directory modifications, while slave servers receive replicated updates through carefully orchestrated synchronization processes that preserve data integrity and minimize service interruptions.
Consumer servers play pivotal roles in distributed architectures by receiving and processing replicated directory updates from designated supplier servers. These consumers can operate in different modes depending on organizational requirements, including read-only configurations for query optimization and specialized replica hubs that facilitate cascading replication scenarios across multiple organizational tiers.
Replica hub configurations enable sophisticated replication topologies where intermediate servers receive updates from master instances and subsequently distribute these changes to additional downstream consumers. This hierarchical approach reduces network bandwidth consumption and improves replication efficiency in large-scale deployments spanning multiple geographical regions or organizational divisions.
One-shot mode replication provides specialized functionality for scenarios requiring immediate, synchronized updates across all directory replicas. This mode ensures atomic consistency during critical directory modifications, preventing temporary inconsistencies that might occur during normal asynchronous replication processes.
LDAP referrals represent sophisticated mechanisms for directing client queries to appropriate directory servers when requested information resides on alternative instances. Referral configurations enable transparent directory distribution while maintaining seamless client experiences across complex, multi-server architectures.
Syncrepl represents the contemporary approach to OpenLDAP replication, replacing legacy slurpd mechanisms with more efficient, reliable synchronization protocols. This pull-based replication methodology enables consumer servers to actively request updates from supplier instances, providing better control over replication timing and reducing network overhead in distributed environments.
Push-based synchronization represents alternative replication approaches where supplier servers actively distribute updates to designated consumers. This methodology proves advantageous in scenarios requiring immediate propagation of critical directory modifications across all organizational replicas.
RefreshOnly and refreshAndPersist represent distinct operational modes within syncrepl configurations. RefreshOnly mode performs periodic synchronization cycles at predetermined intervals, while refreshAndPersist maintains persistent connections enabling real-time update propagation as directory modifications occur.
Replication log analysis provides essential insights into synchronization processes, enabling administrators to monitor replication health, identify potential bottlenecks, and troubleshoot synchronization failures. Understanding replog structures and content interpretation facilitates proactive maintenance and optimization of directory replication infrastructures.
Directory Security and Access Protection Mechanisms
Securing LDAP directories requires comprehensive implementation of encryption protocols, authentication mechanisms, and access control policies that protect sensitive organizational information from unauthorized disclosure or modification. SSL and TLS encryption provide foundational security layers protecting directory communications from interception and manipulation during transmission across network infrastructures.
Transport Layer Security implementation involves configuring appropriate certificate authorities, server certificates, and client authentication credentials that establish trusted communication channels between directory clients and servers. Proper certificate management ensures ongoing security while maintaining operational efficiency across diverse client populations.
Firewall considerations encompass network-level protection mechanisms that control access to directory services based on source addresses, port configurations, and protocol specifications. Strategic firewall implementations provide defense-in-depth security while ensuring legitimate directory access remains unimpeded for authorized users and applications.
Unauthenticated access methods require careful consideration within enterprise environments, as anonymous directory queries may expose sensitive organizational information to unauthorized parties. Implementing appropriate access controls and limiting anonymous query capabilities helps maintain directory security while supporting legitimate operational requirements.
User and password authentication methods encompass various approaches including simple bind operations, SASL mechanisms, and integrated authentication protocols that verify client identities before granting directory access. Selecting appropriate authentication methodologies depends on organizational security requirements and existing infrastructure constraints.
SASL user database maintenance involves managing authentication credentials and associated metadata that support advanced authentication mechanisms including Kerberos integration, GSSAPI protocols, and other enterprise authentication systems. Proper SASL configuration enables seamless integration with existing organizational authentication infrastructures.
Client and server certificate management encompasses comprehensive lifecycle administration including certificate generation, distribution, renewal, and revocation processes that maintain ongoing security across directory infrastructures. Automated certificate management reduces administrative overhead while ensuring consistent security policy enforcement.
Security Strength Factors represent quantitative measures of authentication and encryption strength that guide security policy implementation and compliance verification. Understanding SSF calculations enables administrators to implement appropriate security measures based on organizational risk assessments and regulatory requirements.
Proxy authorization mechanisms enable trusted applications and services to perform directory operations on behalf of authenticated users while maintaining audit trails and access controls. Implementing secure proxy authorization requires careful configuration of trust relationships and privilege delegation policies.
StartTLS represents a protocol extension enabling opportunistic encryption upgrade of initially unencrypted LDAP connections. This approach provides flexible security implementation while maintaining compatibility with legacy applications that may not support initial SSL/TLS connections.
Performance Optimization and Tuning Strategies
OpenLDAP performance optimization requires systematic analysis of server workloads, query patterns, and resource utilization characteristics to identify bottlenecks and implement targeted improvements. Performance measurement encompasses various metrics including query response times, concurrent connection handling, and resource consumption patterns that guide optimization efforts.
Index configuration represents one of the most impactful performance optimization strategies, enabling rapid query resolution through precomputed attribute value mappings. Understanding index types, including equality, presence, substring, and approximate indexes, allows administrators to optimize query performance based on application-specific access patterns.
Database backend optimization involves configuring underlying storage mechanisms to maximize performance while maintaining data integrity and reliability. Berkeley DB configuration parameters significantly impact directory performance, requiring careful tuning based on workload characteristics and hardware capabilities.
Memory allocation and buffer management directly influence directory performance, particularly during high-concurrency scenarios involving numerous simultaneous client connections. Optimizing memory usage patterns reduces disk I/O requirements and improves overall system responsiveness.
Query optimization encompasses various strategies including search base selection, filter construction, and result size limitations that minimize server resource consumption while delivering required information efficiently. Understanding query execution patterns enables administrators to identify and address performance bottlenecks proactively.
Concurrent connection management involves balancing server resources against client connectivity requirements, ensuring adequate performance for all users while preventing resource exhaustion scenarios that might impact service availability. Thread pool configuration and connection limiting mechanisms provide essential tools for managing server capacity.
Disk I/O optimization encompasses storage configuration strategies including RAID implementations, filesystem selection, and disk layout optimization that minimize storage-related performance bottlenecks. Strategic storage design significantly impacts directory performance, particularly during write-intensive operations.
Network optimization considerations include connection pooling, persistent connections, and protocol-level optimizations that reduce communication overhead between directory clients and servers. Efficient network utilization improves user experience while reducing server resource requirements.
Database maintenance operations including regular compaction, index rebuilding, and obsolete entry removal ensure ongoing performance optimization while preventing gradual performance degradation over time. Scheduled maintenance procedures maintain optimal directory performance throughout operational lifecycles.
Monitoring and alerting mechanisms provide ongoing visibility into directory performance characteristics, enabling proactive identification and resolution of emerging performance issues before they impact user experience. Comprehensive monitoring strategies encompass server metrics, query performance, and resource utilization patterns.
Authentication Backend Integration and Implementation
LDAP integration with PAM (Pluggable Authentication Modules) enables centralized authentication services across diverse Unix and Linux environments while maintaining consistent user account management and security policy enforcement. PAM configuration requires understanding module stacking, control flags, and authentication flow patterns that govern user authentication processes.
NSS (Name Service Switch) integration extends LDAP functionality beyond authentication to include user information retrieval, group membership resolution, and other directory-based services that support comprehensive identity management across organizational systems. NSS configuration enables transparent directory integration without requiring application modifications.
Authentication module configuration varies across different Unix environments, requiring platform-specific understanding of PAM implementations, module availability, and configuration syntax variations. Successful multi-platform authentication requires careful attention to environmental differences and compatibility considerations.
System integration testing ensures proper authentication functionality across all supported platforms and applications, identifying potential compatibility issues and configuration problems before production deployment. Comprehensive testing strategies encompass various authentication scenarios and edge cases that might impact user experience.
Directory schema considerations encompass attribute definitions, object class structures, and access control policies that support authentication requirements while maintaining directory organization and security. Proper schema design facilitates efficient authentication processes while supporting organizational information management requirements.
User account provisioning and deprovisioning processes require integration between directory services and organizational identity management systems, ensuring timely account lifecycle management while maintaining security and compliance requirements. Automated provisioning reduces administrative overhead while improving security through consistent policy enforcement.
Group membership management encompasses dynamic group evaluation, nested group support, and group-based access controls that enable sophisticated authorization policies based on organizational structures and functional requirements. Efficient group management reduces administrative complexity while supporting fine-grained access control implementations.
Password policy enforcement through LDAP enables centralized password management including complexity requirements, expiration policies, and history tracking that ensures consistent security policy application across organizational systems. Integrated password management improves security while simplifying user experience.
Single sign-on capabilities enable users to authenticate once and access multiple organizational resources without additional authentication prompts, improving user productivity while maintaining security through centralized authentication controls. SSO implementation requires careful coordination between authentication systems and target applications.
Advanced LDAP Integration and Cross-Platform Authentication
Integrating LDAP with Active Directory and Kerberos represents a sophisticated undertaking that enables seamless authentication across heterogeneous environments while maintaining security and operational efficiency. Kerberos authentication protocols provide robust security mechanisms through ticket-based authentication that eliminates password transmission across network infrastructures.
Cross-platform authentication scenarios require careful consideration of protocol compatibility, realm configuration, and trust relationship establishment between disparate authentication systems. Understanding Kerberos realm hierarchies and cross-realm authentication enables implementation of sophisticated authentication architectures spanning multiple organizational domains.
Single sign-on implementations leverage Kerberos ticket-granting mechanisms to provide seamless user experiences across multiple applications and services without requiring repeated authentication prompts. SSO configurations require precise synchronization between authentication providers and careful management of service principal names and keytab distributions.
Active Directory integration challenges encompass schema differences, attribute mapping requirements, and protocol compatibility considerations that must be addressed to achieve successful interoperability. Understanding Active Directory's LDAP implementation quirks and extensions enables effective integration strategies while avoiding common pitfalls.
DNS configuration plays a crucial role in Kerberos and Active Directory integration, as service discovery mechanisms rely on properly configured DNS records including SRV records, A records, and reverse lookup capabilities. Incorrect DNS configuration frequently causes authentication failures and service discovery problems.
Compatibility limitations between OpenLDAP and Active Directory require careful planning and testing to identify potential issues before production implementation. Understanding these limitations enables development of workaround strategies and alternative approaches that achieve desired functionality while maintaining system stability.
Authentication flow optimization involves configuring referral mechanisms, replica placement, and caching strategies that minimize authentication latency while maintaining security requirements. Strategic authentication infrastructure design improves user experience while reducing server load and network traffic.
Security considerations encompass encryption requirements, credential protection mechanisms, and audit trail implementations that ensure authentication security while maintaining compliance with organizational policies and regulatory requirements. Comprehensive security implementation protects against various attack vectors while maintaining operational efficiency.
Trust relationship management involves establishing and maintaining authentication trust between different domains and realms, enabling users from one organization to access resources in partner organizations through federated authentication mechanisms. Trust relationships require ongoing maintenance and security monitoring.
Troubleshooting cross-platform authentication issues requires understanding protocol interactions, log file analysis, and network traffic examination techniques that enable rapid identification and resolution of authentication problems. Systematic troubleshooting approaches minimize downtime and user impact during authentication service issues.
Samba Architecture and Component Understanding
Samba architecture encompasses multiple interconnected daemons and components that collectively provide SMB/CIFS protocol support, enabling seamless file and print sharing between Linux systems and Windows clients. Understanding the roles and interactions of these components is essential for successful implementation and maintenance of mixed environment infrastructures.
The smbd daemon handles SMB/CIFS protocol communications, managing file and print sharing services while enforcing access controls and maintaining session state information. This daemon processes client connections, authenticates users, and coordinates file access operations while maintaining compatibility with various Windows client versions.
The nmbd daemon provides NetBIOS name service functionality, handling name resolution requests and maintaining browse lists that enable network neighborhood discovery. This component implements WINS functionality and manages browser elections that determine which systems provide directory services for network segments.
The samba daemon, introduced with Samba4, provides Active Directory Domain Controller functionality including DNS services, Kerberos authentication, and LDAP directory services. This unified daemon replaces multiple separate services while providing comprehensive domain controller capabilities compatible with Windows environments.
Winbind service enables integration with Windows domain authentication systems, allowing Linux systems to participate as domain members while utilizing Windows-based user and group authentication. Winbind translates between Windows security identifiers and Unix user/group identifiers while providing seamless authentication experiences.
TCP and UDP port configurations require careful attention to ensure proper SMB/CIFS functionality across network infrastructures. Standard ports including 139, 445, 137, and 138 must be accessible between clients and servers while maintaining appropriate firewall protections against unauthorized access attempts.
Heterogeneous network considerations encompass various challenges including protocol version compatibility, character encoding differences, and naming convention variations that must be addressed to achieve successful cross-platform integration. Understanding these challenges enables implementation of robust solutions that function reliably across diverse environments.
Samba3 and Samba4 architectural differences represent significant evolutionary changes in functionality and implementation approaches. Samba4 introduced comprehensive Active Directory compatibility while maintaining backward compatibility with Samba3 configurations, requiring careful migration planning for existing installations.
Configuration parameter understanding enables administrators to optimize Samba performance and functionality based on specific organizational requirements and environmental constraints. Mastering configuration options facilitates implementation of sophisticated sharing scenarios while maintaining security and performance requirements.
Security model implementation encompasses authentication mechanisms, access controls, and encryption options that protect shared resources while maintaining compatibility with Windows security expectations. Understanding Samba security models enables implementation of appropriate protection mechanisms based on organizational risk assessments.
Samba Configuration Management and Optimization
Comprehensive Samba configuration involves understanding the hierarchical structure of configuration parameters, variable substitutions, and section-specific settings that govern daemon behavior and resource sharing policies. The smb.conf configuration file serves as the central control point for all Samba services, requiring careful organization and documentation to maintain manageable configurations.
Configuration file structure encompasses global parameters that affect all services and share-specific parameters that govern individual resource sharing policies. Understanding parameter precedence and inheritance rules enables efficient configuration management while avoiding conflicts and unexpected behavior patterns.
Variable substitution mechanisms enable dynamic configuration adaptation based on client characteristics, user identities, and environmental conditions. Utilizing variables such as %U for username, %m for client machine name, and %I for client IP address enables creation of flexible configurations that adapt automatically to changing conditions.
Parameter validation through testparm utility provides essential configuration verification capabilities, identifying syntax errors, parameter conflicts, and potential security issues before configuration deployment. Regular configuration validation prevents service disruptions and ensures ongoing configuration integrity.
Secrets database management encompasses encryption key storage, machine account credentials, and trust relationship information that enable domain integration and secure authentication. Understanding secrets.tdb structure and maintenance procedures ensures ongoing security while enabling troubleshooting of authentication issues.
Advanced configuration techniques include include file mechanisms, conditional parameter application, and dynamic configuration generation that enable sophisticated deployment scenarios across large organizations. These techniques reduce configuration complexity while maintaining consistency across multiple server instances.
Performance tuning parameters encompass connection handling, memory allocation, and I/O optimization settings that improve server responsiveness under various load conditions. Understanding performance-related parameters enables optimization based on specific workload characteristics and hardware capabilities.
Security configuration encompasses authentication requirements, encryption settings, and access control policies that protect shared resources while maintaining usability. Implementing appropriate security measures requires balancing protection requirements against functional and performance considerations.
Logging configuration provides essential visibility into Samba operations, enabling monitoring, troubleshooting, and security auditing capabilities. Understanding log levels and output formatting options enables implementation of comprehensive logging strategies that support operational requirements without overwhelming storage resources.
Configuration backup and versioning strategies ensure configuration changes can be reversed and historical configurations can be restored when necessary. Implementing systematic configuration management practices prevents configuration drift and enables rapid recovery from configuration errors.
Maintenance, Monitoring, and Troubleshooting Procedures
Regular Samba maintenance encompasses various activities including log rotation, database cleanup, and performance monitoring that ensure ongoing service reliability and optimal performance. Systematic maintenance procedures prevent gradual service degradation while identifying potential issues before they impact user experience.
Daemon monitoring involves tracking process status, resource utilization, and service responsiveness to identify performance bottlenecks and potential failures. Understanding normal operational parameters enables early detection of abnormal conditions that might indicate emerging problems requiring attention.
The smbcontrol utility provides administrative control capabilities for running Samba daemons, enabling configuration reloading, debug level adjustment, and service status queries without requiring service interruption. Mastering smbcontrol functionality enables efficient administrative operations while minimizing service disruptions.
Service status monitoring through smbstatus reveals current connection information, locked files, and resource utilization patterns that provide insights into service usage and potential performance issues. Regular status monitoring enables proactive capacity planning and performance optimization.
TDB file management encompasses backup procedures, corruption detection, and recovery strategies for Samba database files that store critical service information. Understanding TDB file structures and maintenance requirements prevents data loss while enabling recovery from corruption scenarios.
Database backup procedures using tdbbackup ensure critical Samba configuration and state information can be preserved and restored when necessary. Regular backup schedules protect against data loss while enabling rapid recovery from various failure scenarios.
Corruption detection and recovery procedures enable identification and remediation of database corruption issues that might affect service functionality. Understanding corruption symptoms and recovery procedures minimizes service disruption while preserving data integrity.
Content manipulation through tdbdump, tdbrestore, and tdbtool utilities enables administrative access to database contents for troubleshooting and recovery purposes. These tools provide essential capabilities for resolving complex configuration and authentication issues.
Log analysis techniques encompass understanding log formats, identifying significant events, and correlating log entries across multiple services to diagnose complex problems. Systematic log analysis enables rapid problem identification and resolution while building operational knowledge.
Troubleshooting methodologies encompass systematic approaches to problem identification, isolation, and resolution that minimize downtime while ensuring complete problem resolution. Understanding common problem patterns and diagnostic techniques enables efficient troubleshooting across various scenarios.
Internationalization and Share Configuration Management
Internationalization within mixed environments presents complex challenges related to character encoding, naming conventions, and cultural considerations that must be addressed to ensure seamless operation across diverse linguistic and regional contexts. Understanding character code systems and their implications for file naming, user identification, and system integration enables successful deployment in multinational organizational environments.
Character code systems including ASCII, UTF-8, Unicode, and various legacy encodings represent different approaches to character representation that impact how systems interpret and display textual information. Each encoding system has specific characteristics and limitations that influence compatibility between different platforms and applications, requiring careful consideration during system integration planning.
Code page configurations determine how Windows systems interpret and display characters, particularly for languages requiring extended character sets beyond basic ASCII. Understanding code page relationships and conversion mechanisms enables proper configuration of Samba systems to maintain character integrity across platform boundaries.
Namespace differences between Windows and Linux systems create significant challenges for international deployments, as each platform has different rules and restrictions for file names, directory names, and user identifications. Windows systems typically support longer filenames with different character restrictions compared to traditional Unix systems, requiring careful mapping and conversion strategies.
Share naming conventions must accommodate international character requirements while maintaining compatibility with various client systems that may have different character set support capabilities. Strategic naming approaches avoid compatibility problems while supporting organizational requirements for multilingual resource identification.
File and directory naming considerations encompass character set support, length limitations, and reserved character handling across different platforms. Understanding these constraints enables development of naming policies that function reliably across all supported client systems while meeting organizational requirements.
User and group naming policies must account for international characters, diacritical marks, and various cultural naming conventions while maintaining system compatibility and security requirements. Implementing flexible naming policies accommodates diverse organizational populations while avoiding system limitations and conflicts.
Computer naming strategies require coordination between various naming systems including NetBIOS names, DNS hostnames, and Kerberos principals that may have different character set restrictions and formatting requirements. Consistent naming approaches simplify administration while ensuring reliable name resolution across all supported protocols.
Character set conversion mechanisms enable translation between different encoding systems, preserving textual content while adapting to platform-specific requirements. Understanding conversion processes and potential data loss scenarios enables implementation of robust internationalization strategies.
Configuration parameters including dos charset, display charset, and unix charset control character encoding behavior within Samba, enabling proper handling of international content while maintaining compatibility with various client systems. Proper charset configuration prevents character corruption and display problems.
File Service Configuration and Access Management
File service implementation encompasses comprehensive sharing strategies that accommodate diverse organizational requirements while maintaining security, performance, and administrative efficiency. Creating and configuring file shares involves understanding access controls, permission models, and integration mechanisms that enable seamless file access across heterogeneous client populations.
Share configuration encompasses various parameters including browsability settings, write permissions, and user access controls that govern how clients interact with shared resources. Understanding these parameters enables implementation of sophisticated sharing policies that meet specific organizational requirements while maintaining security boundaries.
Migration planning for file services requires careful assessment of existing file structures, permission models, and usage patterns to develop migration strategies that minimize disruption while preserving data integrity and access controls. Systematic migration approaches ensure business continuity throughout transition processes.
IPC$ share management presents special security considerations as this administrative share provides access to named pipes and other system resources. Limiting IPC$ access prevents unauthorized system exploration while maintaining necessary functionality for legitimate administrative operations and applications.
Script development for user and group handling enables automation of routine administrative tasks while ensuring consistent policy application across large user populations. Understanding scripting interfaces and available APIs enables creation of sophisticated management tools that reduce administrative overhead.
Access control parameters including browseable, writeable, valid users, write list, read list, read only, and guest ok provide granular control over resource access permissions. Mastering these parameters enables implementation of complex access policies that support organizational requirements while maintaining security boundaries.
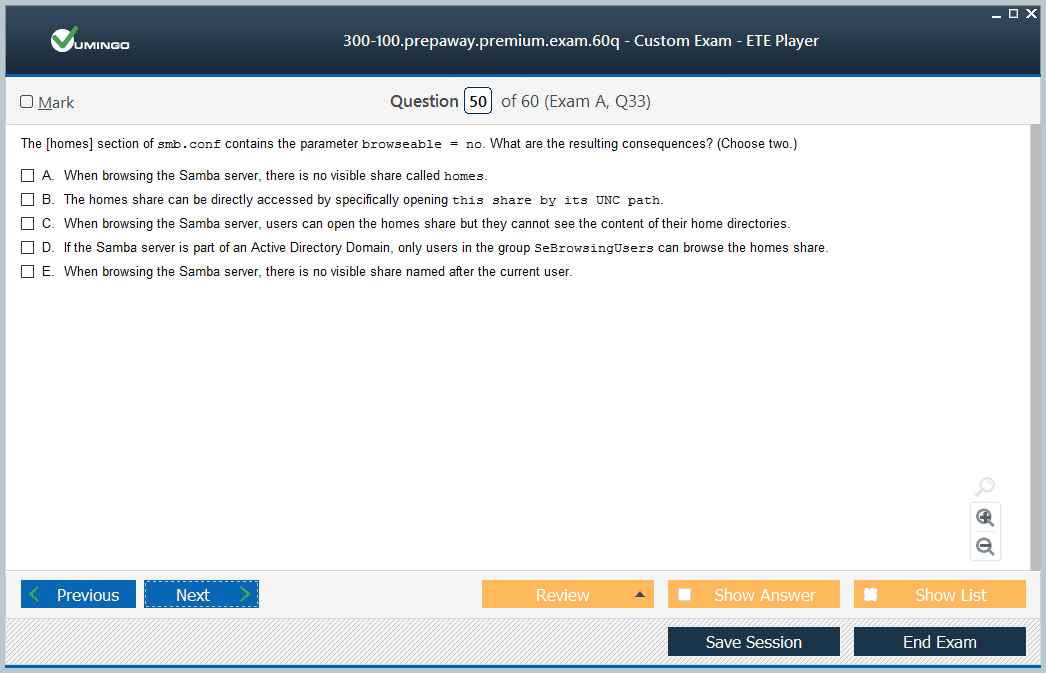
The [homes] share provides automatic home directory access for authenticated users, enabling personalized storage space while maintaining centralized administration. Configuring [homes] requires understanding user mapping, path substitution, and permission inheritance to ensure proper functionality across diverse user populations.
Quota management through smbcquotas enables disk usage limitations and monitoring that prevent resource exhaustion while providing usage visibility to administrators and users. Implementing quota policies requires understanding filesystem quota support and integration with Samba permission models.
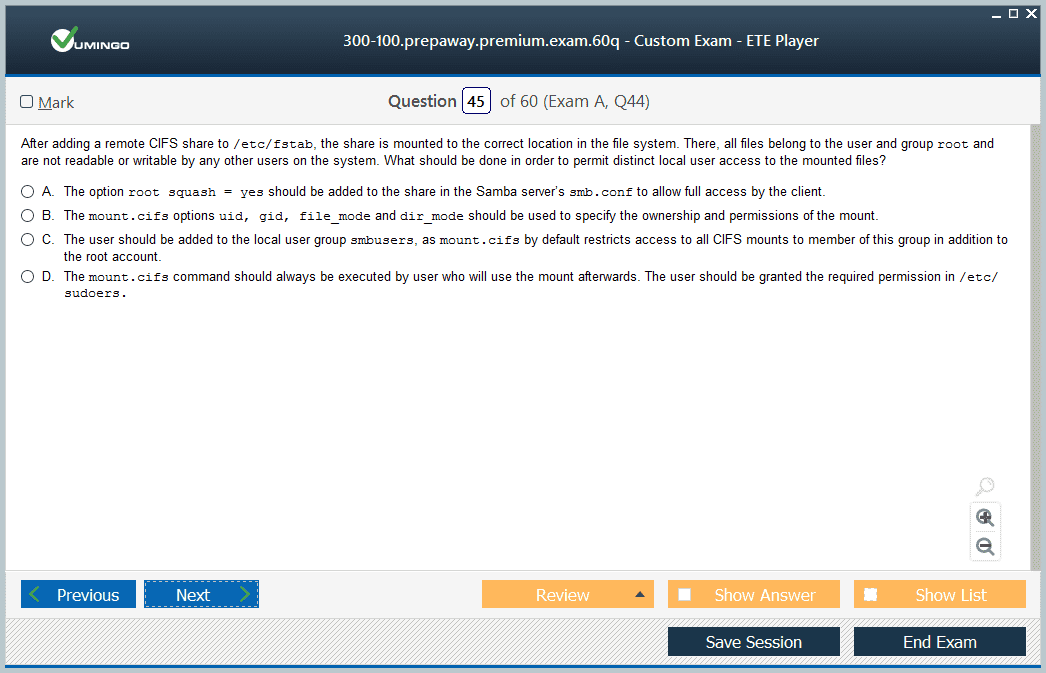
Remote access mechanisms including smbmount and cifs mount options enable Linux clients to access Samba shares as local filesystems, providing transparent file access while maintaining proper permission and ownership mappings. Understanding mount options and their security implications enables secure and efficient remote filesystem access.
Network browsing configuration affects how shares appear in network neighborhood displays and other discovery mechanisms used by Windows clients. Strategic browsing configuration balances resource visibility against security considerations while supporting user productivity and system discovery requirements.
Permission Models and Access Control Integration
Linux filesystem permissions interact with Samba access controls through complex mapping mechanisms that require deep understanding to implement effective security policies. The interaction between Unix permissions, Samba access parameters, and Windows security models creates layered security systems that must be carefully configured to achieve desired access control outcomes.
Permission control mechanisms encompass traditional Unix permissions, POSIX ACLs, and Windows-style access control lists that provide different levels of granularity and functionality. Understanding the relationships and interactions between these permission models enables implementation of sophisticated access control policies that meet diverse organizational requirements.
Samba's interaction with Linux filesystem permissions involves permission mapping, ownership handling, and access determination processes that translate between different permission models. Understanding these interactions enables prediction and control of access behavior across different client types and authentication mechanisms.
Access Control List storage through Samba VFS modules enables preservation of Windows ACL information within Linux filesystems, maintaining detailed permission information while supporting advanced Windows security features. VFS ACL modules including vfs_acl_xattr and vfs_acl_tdb provide different storage approaches with varying performance and compatibility characteristics.
Create mask and directory mask parameters control default permissions assigned to newly created files and directories, enabling consistent permission application while supporting organizational security policies. Understanding mask interactions with user permissions and Windows security expectations enables implementation of appropriate default security settings.
Force create mode and force directory mode parameters provide administrative override capabilities for permission assignment, ensuring consistent permission application regardless of client-specified permissions. These parameters enable enforcement of organizational security policies while maintaining compatibility with various client applications.
Security descriptor handling involves translation between Windows security descriptors and Linux permission models, maintaining security information integrity while supporting cross-platform access. Understanding security descriptor structures and mapping mechanisms enables troubleshooting of complex permission issues.
The smbcacls utility provides command-line access control management capabilities, enabling administrative manipulation of Windows-style ACLs on Samba shares. Mastering smbcacls functionality enables efficient permission management and troubleshooting of access control issues without requiring Windows client access.
POSIX ACL integration through getfacl and setfacl utilities enables advanced permission management that exceeds traditional Unix permission capabilities while maintaining compatibility with Samba access controls. Understanding POSIX ACL interaction with Samba enables implementation of sophisticated permission policies.
VFS object configuration enables loading of specialized modules that extend Samba functionality including ACL storage, audit logging, and content filtering capabilities. Understanding VFS architecture and available modules enables implementation of advanced features that support specific organizational requirements.
Print Service Integration and Management
Print service configuration within mixed environments requires understanding of printing protocols, driver management, and client configuration requirements that enable seamless printing across heterogeneous client populations. Integrating Samba with CUPS (Common Unix Printing System) creates comprehensive printing solutions that support various client types while maintaining centralized administration.
Printer sharing configuration encompasses share definitions, access controls, and driver management policies that govern how clients access and utilize printing resources. Understanding print share parameters enables implementation of sophisticated printing policies that control access while supporting diverse client requirements.
CUPS integration involves configuring print queue definitions, driver associations, and access controls within the CUPS printing system while coordinating these settings with Samba share configurations. Successful integration requires understanding both CUPS and Samba printing architectures and their interaction mechanisms.
Windows print driver management encompasses driver storage, distribution, and installation mechanisms that enable automatic client configuration while reducing administrative overhead. The [print$] share provides centralized driver storage while supporting Point and Print driver installation mechanisms used by Windows clients.
Driver uploading procedures using Windows Add Print Driver Wizard enable centralized driver management while supporting automatic client driver installation. Understanding driver upload processes and requirements enables implementation of streamlined printing environments that minimize client-side configuration requirements.
Print queue management involves coordinating between Samba print shares and underlying CUPS print queues, ensuring proper job routing and status reporting while maintaining access controls. Understanding queue mapping and job handling enables troubleshooting of complex printing issues.
Security considerations for print sharing encompass access controls, driver security, and audit requirements that protect printing resources while preventing unauthorized access or misuse. Implementing appropriate print security requires understanding various attack vectors and protection mechanisms available within printing infrastructures.
Spooling directory configuration including /var/spool/samba controls temporary storage for print jobs while they await processing, requiring proper permissions and space allocation to ensure reliable printing operation. Understanding spooling requirements enables optimization of printing performance and reliability.
The smbspool utility provides backend printing support for CUPS, enabling integration between CUPS print queues and SMB/CIFS printing protocols. Understanding smbspool configuration and operation enables troubleshooting of printing connectivity issues between different systems.
Print driver compatibility considerations encompass various Windows versions, printer types, and driver architectures that must be supported to ensure comprehensive client compatibility. Understanding driver compatibility requirements enables selection and deployment of appropriate printing solutions across diverse client populations.
User Management and Domain Integration Strategies
Managing user accounts and groups within mixed environments requires comprehensive understanding of identity synchronization, mapping mechanisms, and authentication integration that enables seamless user experience across heterogeneous systems. User account management encompasses provisioning, modification, and deprovisioning processes that maintain security while supporting operational efficiency.
The pdbedit utility provides essential user account management capabilities within Samba environments, enabling creation, modification, and deletion of user accounts while maintaining appropriate database consistency. Understanding pdbedit functionality enables efficient user administration while ensuring proper account configuration and security policy enforcement.
User and group mapping mechanisms translate between different identity systems including Windows security identifiers, Unix user identifiers, and LDAP distinguished names. Proper mapping configuration ensures consistent identity representation across different systems while maintaining access control integrity and audit trail accuracy.
Account management tools encompass various utilities including samba-tool user and samba-tool group commands that provide comprehensive identity management capabilities for Samba4 environments. These tools support Active Directory-compatible user and group administration while maintaining integration with underlying Linux identity systems.
The smbpasswd program enables password management for Samba user accounts, supporting password changes, account activation/deactivation, and password policy enforcement. Understanding smbpasswd functionality enables implementation of comprehensive password management policies while maintaining user accessibility and security requirements.
File and directory ownership enforcement through force user and force group parameters enables consistent ownership assignment regardless of client-specified ownership. These parameters support organizational security policies while simplifying permission management across diverse user populations and access patterns.
Unix identity integration involves coordination between /etc/passwd, /etc/group, and Samba user databases to ensure consistent identity representation across all system components. Proper integration eliminates identity conflicts while maintaining compatibility with both Unix applications and Windows clients.
Identity mapping (idmap) configuration enables translation between Windows security identifiers and Unix user/group identifiers, maintaining consistent identity representation while supporting various mapping strategies including static assignments, algorithmic generation, and directory-based lookups.
Account lifecycle management encompasses automated provisioning and deprovisioning processes that maintain account security while reducing administrative overhead. Understanding integration points with identity management systems enables implementation of efficient account management workflows that support organizational policies.
Group membership management involves maintaining group assignments across multiple identity systems while supporting nested groups, dynamic membership, and complex organizational hierarchies. Effective group management simplifies access control administration while supporting sophisticated organizational requirements.
Authentication and Authorization Framework Implementation
Authentication mechanism implementation encompasses various approaches including local databases, directory integration, and external authentication systems that provide flexible authentication options while maintaining security and performance requirements. Understanding authentication flows and integration points enables implementation of robust authentication architectures.
Local password database setup involves configuring Samba-specific user accounts and authentication credentials that provide self-contained authentication services without requiring external dependencies. Local databases support smaller organizations or isolated environments while maintaining full authentication functionality.
Password synchronization mechanisms enable coordination between multiple authentication systems, ensuring users maintain consistent passwords across different services while reducing administrative complexity. Synchronization strategies must balance security requirements against user experience considerations.
Passdb backend configuration determines how Samba stores and retrieves authentication information, with options including smbpasswd files, tdbsam databases, and ldapsam integration. Understanding backend characteristics and performance implications enables selection of appropriate storage mechanisms based on organizational requirements.
Backend conversion procedures enable migration between different passdb storage mechanisms while preserving user accounts and authentication information. Understanding conversion processes and potential limitations enables successful migration planning and execution.
LDAP integration enables centralized authentication services while supporting sophisticated identity management capabilities including group membership, password policies, and account provisioning workflows. Proper LDAP integration requires understanding schema requirements and attribute mapping mechanisms.
Winbind service configuration enables integration with Windows domain authentication while providing Unix identity services for domain users and groups. Winbind configuration encompasses NSS and PAM integration that enables transparent domain authentication across Linux systems.
NSS configuration through libnss_winbind enables resolution of domain users and groups through standard Unix identity mechanisms, providing transparent domain integration without requiring application modifications. Understanding NSS configuration and troubleshooting enables successful domain member implementation.
PAM integration through libpam_winbind enables domain authentication for various system services including login sessions, ssh access, and application authentication. PAM configuration requires understanding module stacking and authentication flow control to ensure proper authentication behavior.
Security identifier management involves handling Windows SIDs and foreign SIDs that identify users and groups across domain boundaries. Understanding SID allocation and mapping mechanisms enables troubleshooting of identity resolution issues and access control problems.
Domain Controller Configuration and Management
Primary Domain Controller implementation using Samba3 and Samba4 provides centralized authentication and policy management for Windows and Linux clients within organizational domains. Understanding PDC requirements and configuration enables implementation of comprehensive domain services that support diverse client populations.
Backup Domain Controller configuration provides redundancy and load distribution for domain services while maintaining synchronization with primary domain controllers. BDC implementation requires understanding replication mechanisms and failover procedures that ensure service continuity during primary controller outages.
Domain membership and trust relationship management encompasses establishment and maintenance of authentication relationships between different domains and forests. Understanding trust mechanisms enables implementation of complex organizational authentication architectures that support business relationships and organizational structures.
Computer account management involves adding workstations and servers to domains while maintaining proper authentication relationships and security policies. Machine account administration ensures proper domain integration while supporting automated deployment and management processes.
Logon script configuration enables automated client configuration during user authentication, providing consistent desktop environments while supporting organizational policies and user productivity requirements. Script deployment requires understanding client capabilities and security implications of automated configuration.
Roaming profile implementation enables users to access personalized desktop environments from multiple workstations while maintaining centralized profile storage and management. Profile configuration requires understanding storage requirements and client compatibility considerations.
System policy deployment through NTConfig.pol enables centralized desktop and security policy enforcement across domain clients. Policy implementation requires understanding client support and policy precedence mechanisms that govern policy application.
The net command provides comprehensive domain management capabilities including user administration, group management, and trust relationship configuration. Understanding net command functionality enables efficient domain administration while supporting complex organizational requirements.
Profile management encompasses creation, modification, and maintenance of user profiles while ensuring proper permissions and access controls. Profile administration requires understanding Windows profile structures and compatibility requirements across different client versions.
Machine account scripting through add machine script enables automated workstation joining while maintaining proper security controls and audit trails. Script implementation supports large-scale deployment scenarios while reducing administrative overhead.
Advanced Domain Integration and Active Directory Compatibility with Samba4
The integration of Samba4 as an Active Directory Domain Controller (AD DC) has revolutionized the landscape of domain management by providing comprehensive Windows domain services, including DNS, Kerberos, and LDAP. With Samba4, IT professionals can build and manage sophisticated domain infrastructures that are fully compatible with native Windows implementations, offering seamless integration for both Windows and non-Windows clients. This capability has significantly lowered the barrier to creating cost-effective, flexible, and secure domain environments while maintaining the robust functionality that organizations have come to rely on from Windows Server-based solutions.
Samba4's AD DC implementation is particularly beneficial for organizations looking to maintain interoperability between Windows-based and Linux/Unix-based systems within a unified domain environment. This means that businesses can take advantage of open-source solutions while still ensuring compatibility with legacy systems and modern Windows clients. To fully appreciate the power and flexibility of Samba4 in this context, it is essential to understand the key components involved in configuring, testing, and maintaining a Samba4 AD DC deployment. This article will explore the critical aspects of Samba4 Active Directory functionality, domain services, DNS integration, and troubleshooting tools.
Active Directory Domain Controller Configuration with Samba4
The role of an Active Directory Domain Controller is central to any domain-based network, acting as the central authority for authentication, authorization, and directory services. Configuring Samba4 as an AD DC involves setting up a domain controller that can manage user accounts, permissions, and policies, just as a Windows-based Active Directory Domain Controller does. Samba4 provides a robust set of services, including Kerberos authentication, LDAP directory services, and the DNS server functionality necessary for domain name resolution within the network.
The process of setting up Samba4 as an AD DC begins with the installation and configuration of the Samba package on a Linux-based system. This step involves configuring the Samba server to function as a domain controller, setting up the appropriate Kerberos and LDAP services, and ensuring proper DNS resolution. During this process, it is critical to configure Samba4 with the correct domain name, organizational units, and administrative groups to match the intended network topology and security requirements.
Once Samba4 is installed and configured, administrators must verify that all domain services are operational. This includes checking Kerberos authentication, ensuring that LDAP queries are resolving correctly, and verifying that DNS name resolution works for both internal and external resources. Proper testing and validation are essential to avoid any disruption in services during the production rollout. Samba4's compatibility with standard Windows Active Directory structures means that it can effectively serve as a drop-in replacement for a Windows server, offering seamless integration with Windows-based clients and devices.
DNS Integration and Name Resolution in Samba4
One of the critical components of an Active Directory domain is DNS (Domain Name System). DNS enables the resolution of hostnames to IP addresses, ensuring that clients can locate domain controllers, shared resources, and other network services. Samba4’s integration with DNS is particularly important for ensuring the smooth operation of a domain network. By acting as both the AD DC and the DNS server, Samba4 ensures that DNS records for the domain are dynamically updated as changes occur in the Active Directory database.
Samba4’s internal DNS service automatically updates DNS records for domain controllers, clients, and other network services, making it possible for clients to locate the domain controller using the standard DNS queries. However, in environments where an existing DNS infrastructure is already in place, Samba4 must be carefully integrated with that infrastructure to avoid conflicts and ensure smooth name resolution. This requires configuring the Samba DNS server to forward queries to existing DNS servers for external name resolution while maintaining authoritative control for the internal domain.
For organizations with complex DNS setups, such as those using split-brain DNS or external DNS providers, special attention must be given to ensure that Samba4 can coexist with the current DNS policies. The integration of Samba4 with DNS involves configuring DNS zones, setting up forwarders, and ensuring proper delegation of records. Understanding how DNS integration functions within the context of Samba4 and the existing DNS environment is crucial to ensure that clients can resolve both internal and external addresses reliably.
Kerberos Authentication and Security
Kerberos is an essential component of Active Directory environments, providing a secure method for authenticating users and services over a network. In Samba4, Kerberos authentication is implemented in a way that mimics the behavior of Windows Server domain controllers. This means that Samba4 can authenticate users, services, and machines in the same manner as a Windows-based domain, ensuring that clients do not experience any disruptions when accessing domain resources.
Samba4 provides robust Kerberos authentication, including the ability to generate and issue tickets for services and users. The configuration of Kerberos within Samba4 involves setting up proper realms, configuring ticket-granting ticket (TGT) mechanisms, and ensuring synchronization with domain controllers. This level of authentication security ensures that only authorized users and services can access domain resources, and it helps to maintain a secure and reliable network environment.
Samba4's Kerberos implementation also includes support for cross-realm authentication, allowing organizations to establish trust relationships with other domains or forests. This feature enhances the interoperability of Samba4 with other Active Directory environments, making it easier for organizations to integrate Samba4 into their existing domain infrastructures while maintaining the highest levels of security.
LDAP Directory Services in Samba4
The Lightweight Directory Access Protocol (LDAP) is a protocol used for accessing and managing directory services, such as Active Directory. Samba4 supports LDAP as a core component of its Active Directory implementation, providing the means to store and retrieve information about users, groups, computers, and other network objects. LDAP allows administrators to query and manage the directory database, ensuring that users and resources are correctly represented within the domain.
With Samba4, LDAP functionality is fully compatible with Windows-based AD environments, allowing Samba4 to serve as a central directory service in mixed-platform networks. This means that Samba4 can be used to store information about Windows clients, Linux machines, and other devices, offering a single point of management for all domain resources.
LDAP support in Samba4 is configurable, enabling administrators to define the structure of the directory, including organizational units (OUs), group policies, and user attributes. The flexibility of Samba4’s LDAP implementation allows for fine-grained control over how directory data is organized and accessed. Additionally, Samba4 supports secure LDAP (LDAPS), ensuring that directory communications are encrypted for added security.
Verifying Samba4 Active Directory Operation with smbclient
Once Samba4 is configured as an Active Directory Domain Controller, it is essential to test its functionality to ensure that all services are running correctly. The smbclient utility is a powerful tool for interacting with and verifying Samba4’s integration with Active Directory. This command-line utility allows administrators to connect to and test various aspects of the domain, including authentication, file sharing, and network resource access.
Using smbclient, administrators can perform diagnostic checks to verify that authentication requests are properly processed, ensuring that users can log into the domain without issues. Additionally, smbclient allows for testing access to shared resources, making it easier to diagnose any problems related to file sharing or permissions. By running smbclient against the domain controller, administrators can simulate user logins, group policy application, and resource access, identifying potential issues before they affect the end users.
The smbclient tool also supports a range of troubleshooting options, such as detailed logging, which provides insights into the underlying causes of any authentication or access issues. This makes smbclient an invaluable utility for ensuring the health and reliability of a Samba4-based Active Directory environment.
Conclusion
Despite the robust functionality of Samba4, compatibility issues can arise during implementation, especially in mixed-OS environments. These issues typically manifest in areas such as authentication failures, DNS resolution problems, or policy application errors. Understanding the troubleshooting process and utilizing the available diagnostic tools, such as smbclient and logs, is essential for quickly resolving any issues that may arise.
One common issue is the misconfiguration of Kerberos, which can result in authentication failures. If Kerberos tickets are not being issued correctly, users may not be able to log into the domain or access network resources. Similarly, DNS misconfigurations can lead to clients being unable to find the domain controller, resulting in network connectivity issues. Carefully reviewing Samba4 logs and conducting thorough testing with smbclient can help pinpoint the source of these problems and guide administrators toward an effective solution.
By following best practices for configuration and testing, administrators can ensure that their Samba4 Active Directory deployment runs smoothly, providing reliable and secure domain services for all network clients.
LPI 300-100 practice test questions and answers, training course, study guide are uploaded in ETE Files format by real users. Study and Pass 300-100 LPIC-3 Exam 300: Mixed Environments certification exam dumps & practice test questions and answers are to help students.
- 010-160 - Linux Essentials Certificate Exam, version 1.6
- 102-500 - LPI Level 1
- 101-500 - LPIC-1 Exam 101
- 201-450 - LPIC-2 Exam 201
- 202-450 - LPIC-2 Exam 202
- 300-300 - LPIC-3 Mixed Environments
- 305-300 - Linux Professional Institute LPIC-3 Virtualization and Containerization
- 303-300 - LPIC-3 Security Exam 303
- 010-150 - Entry Level Linux Essentials Certificate of Achievement
Why customers love us?
What do our customers say?
The resources provided for the LPI certification exam were exceptional. The exam dumps and video courses offered clear and concise explanations of each topic. I felt thoroughly prepared for the 300-100 test and passed with ease.
Studying for the LPI certification exam was a breeze with the comprehensive materials from this site. The detailed study guides and accurate exam dumps helped me understand every concept. I aced the 300-100 exam on my first try!
I was impressed with the quality of the 300-100 preparation materials for the LPI certification exam. The video courses were engaging, and the study guides covered all the essential topics. These resources made a significant difference in my study routine and overall performance. I went into the exam feeling confident and well-prepared.
The 300-100 materials for the LPI certification exam were invaluable. They provided detailed, concise explanations for each topic, helping me grasp the entire syllabus. After studying with these resources, I was able to tackle the final test questions confidently and successfully.
Thanks to the comprehensive study guides and video courses, I aced the 300-100 exam. The exam dumps were spot on and helped me understand the types of questions to expect. The certification exam was much less intimidating thanks to their excellent prep materials. So, I highly recommend their services for anyone preparing for this certification exam.
Achieving my LPI certification was a seamless experience. The detailed study guide and practice questions ensured I was fully prepared for 300-100. The customer support was responsive and helpful throughout my journey. Highly recommend their services for anyone preparing for their certification test.
I couldn't be happier with my certification results! The study materials were comprehensive and easy to understand, making my preparation for the 300-100 stress-free. Using these resources, I was able to pass my exam on the first attempt. They are a must-have for anyone serious about advancing their career.
The practice exams were incredibly helpful in familiarizing me with the actual test format. I felt confident and well-prepared going into my 300-100 certification exam. The support and guidance provided were top-notch. I couldn't have obtained my LPI certification without these amazing tools!
The materials provided for the 300-100 were comprehensive and very well-structured. The practice tests were particularly useful in building my confidence and understanding the exam format. After using these materials, I felt well-prepared and was able to solve all the questions on the final test with ease. Passing the certification exam was a huge relief! I feel much more competent in my role. Thank you!
The certification prep was excellent. The content was up-to-date and aligned perfectly with the exam requirements. I appreciated the clear explanations and real-world examples that made complex topics easier to grasp. I passed 300-100 successfully. It was a game-changer for my career in IT!