- Home
- Cisco Certifications
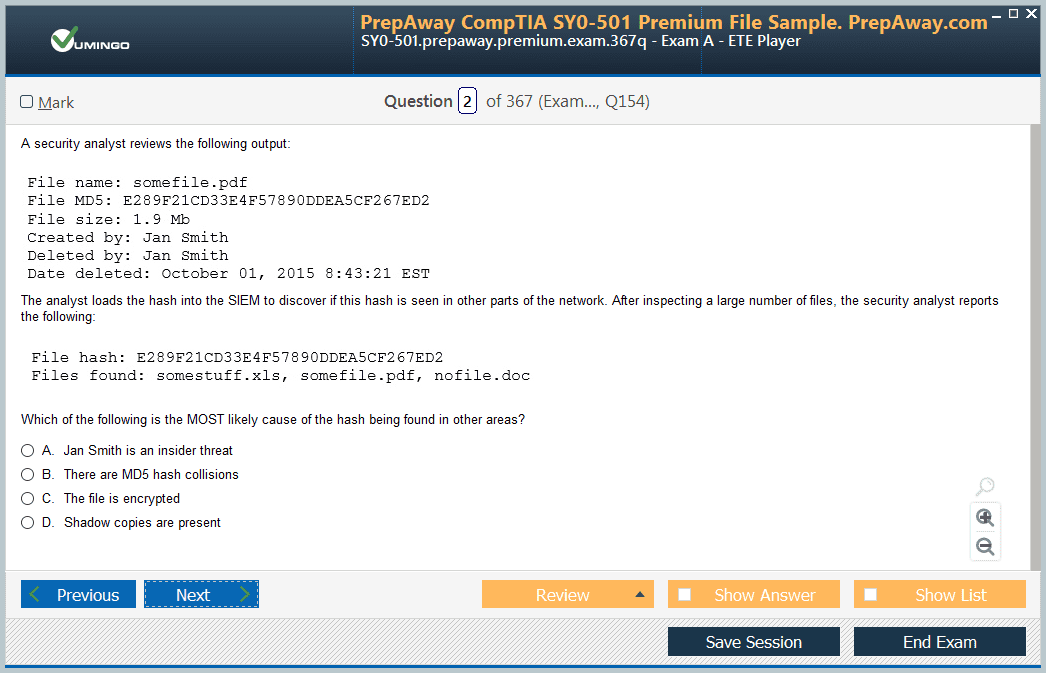
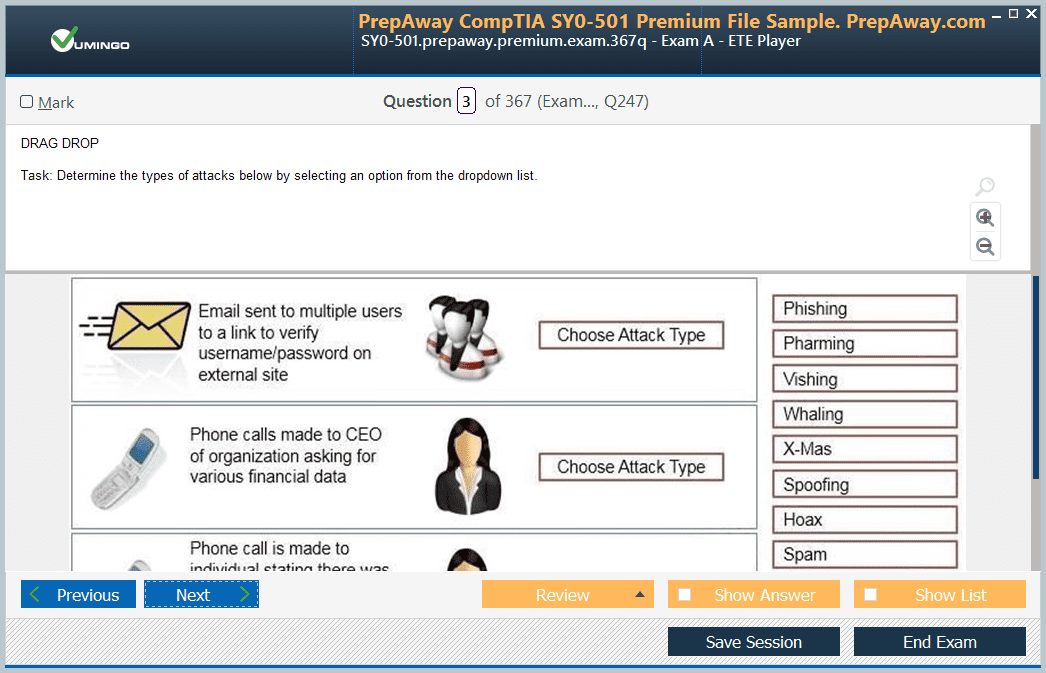
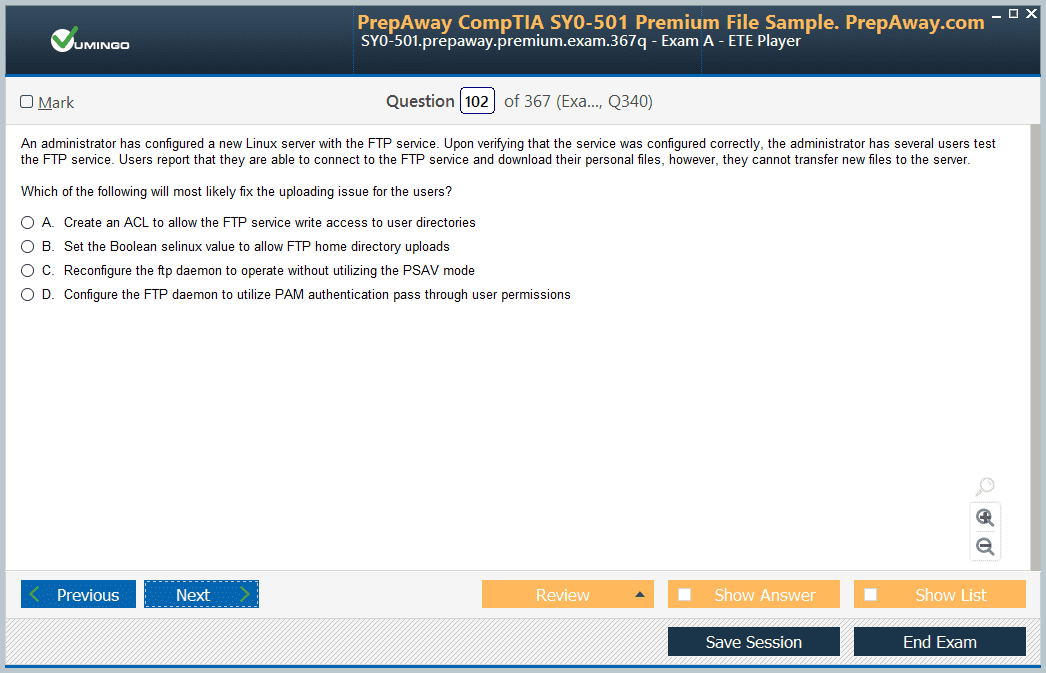
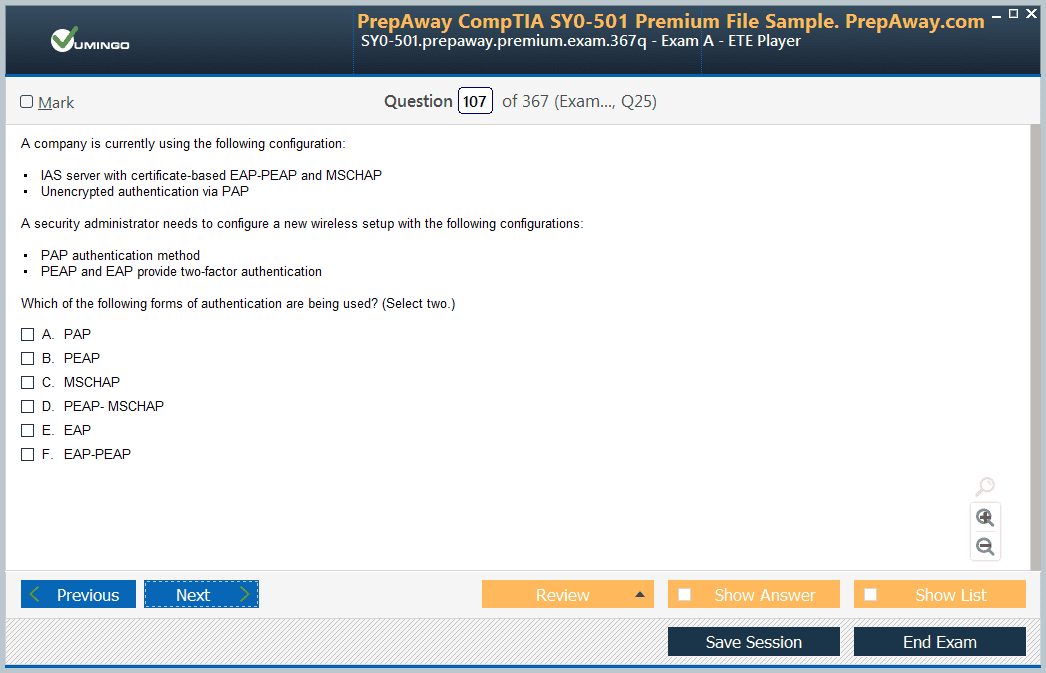
- 300-725 Securing the Web with Cisco Web Security Appliance (300-725 SWSA) Dumps
Pass Cisco SWSA 300-725 Exam in First Attempt Guaranteed!
Get 100% Latest Exam Questions, Accurate & Verified Answers to Pass the Actual Exam!
30 Days Free Updates, Instant Download!


300-725 Premium File
- Premium File 60 Questions & Answers. Last Update: Feb 04, 2026
Whats Included:
- Latest Questions
- 100% Accurate Answers
- Fast Exam Updates
Last Week Results!
All Cisco SWSA 300-725 certification exam dumps, study guide, training courses are Prepared by industry experts. PrepAway's ETE files povide the 300-725 Securing the Web with Cisco Web Security Appliance (300-725 SWSA) practice test questions and answers & exam dumps, study guide and training courses help you study and pass hassle-free!
The Critical Role of Cisco 300-725 SWSA Certification in Contemporary Digital Security
The modern digital threat environment presents organizations with complex challenges requiring sophisticated defense mechanisms against evolving cyber risks. As malicious actors develop increasingly advanced attack methodologies, businesses across all industries must implement robust web-based security solutions to protect their digital assets. The Cisco 300-725 SWSA credential emerges as a premier qualification demonstrating expertise in implementing and managing enterprise-level web security appliances.
This specialized certification validates professionals' capabilities in deploying comprehensive security frameworks that address contemporary threat vectors. Rather than serving as merely another technical qualification, the 300-725 SWSA credential represents mastery of critical security infrastructure components essential for protecting organizational digital ecosystems.
Contemporary business environments have fundamentally shifted from traditional security perimeters to distributed, cloud-centric architectures. Remote workforce models, mobile device integration, and hybrid cloud deployments have created new vulnerability surfaces requiring specialized security expertise. Professionals holding validated web appliance security credentials occupy essential positions within organizational security teams.
The certification specifically validates competency in Cisco's Web Security Appliance platform, a cornerstone technology for enterprise web protection strategies. This advanced security solution provides comprehensive defense against malicious content, unauthorized data access, and various web-borne threats that can compromise organizational integrity.
Examination Structure and Technical Requirements
The Cisco 300-725 examination, officially designated "Securing the Web with Cisco Secure Web Appliance," presents a rigorous assessment of practical knowledge and implementation capabilities required for enterprise web security deployment. This comprehensive evaluation measures both theoretical understanding and hands-on expertise necessary for real-world security implementations.
Test-takers must complete the examination within a ninety-minute timeframe, addressing between fifty-five and sixty-five carefully designed questions that evaluate complex security concepts and practical application scenarios. The assessment format combines traditional multiple-choice inquiries with interactive simulation exercises that replicate authentic deployment environments, ensuring successful candidates possess both conceptual knowledge and implementation experience.
Achievement requires scoring between 750 and 850 points from a total possible score of 1000 points, reflecting rigorous standards maintained throughout Cisco's certification ecosystem. The examination fee is established at 300 USD, representing a reasonable investment considering the substantial professional benefits associated with this prestigious credential.
Testing is conducted exclusively in English through Pearson VUE facilities worldwide, ensuring global accessibility for international candidates seeking to advance their cybersecurity qualifications. The comprehensive examination structure guarantees that successful professionals demonstrate expertise necessary for immediate contribution to organizational security initiatives.
Industry Recognition and Professional Value Proposition
The cybersecurity sector has experienced remarkable expansion, driven by heightened awareness of digital threats and comprehensive regulatory compliance mandates across diverse economic sectors. Healthcare organizations, financial institutions, government agencies, educational establishments, and technology companies actively seek qualified professionals with specialized web security expertise demonstrated through industry-recognized credentials.
Research conducted by leading cybersecurity organizations indicates that approximately sixty-eight percent of hiring managers and technical leadership express strong preference for candidates possessing vendor-specific certifications from established industry leaders. This preference reflects the practical applicability of these credentials and their direct relevance to daily security challenges faced by modern organizations.
The Cisco 300-725 SWSA certification enjoys widespread recognition throughout the cybersecurity community due to Cisco's established reputation as a global leader in networking and security technologies. Organizations with existing Cisco security infrastructure particularly value professionals with validated expertise in these systems, as they can immediately contribute to ongoing security programs without extensive additional training requirements.
Additionally, this certification aligns with current industry trends emphasizing specialized security expertise, as organizations increasingly understand the limitations of generalist cybersecurity approaches. The focused concentration on web appliance security technologies positions certified professionals as valuable organizational assets capable of addressing specific security challenges requiring deep technical knowledge and practical implementation experience.
Detailed Examination Content Areas and Domain Weightings
The Cisco 300-725 SWSA examination encompasses comprehensive technical domains, each weighted according to importance within the complete web appliance security ecosystem. Understanding specific weightings and focus areas enables candidates to allocate preparation time effectively while ensuring thorough coverage of essential topics.
Features and functionality comprise ten percent of the total assessment, requiring candidates to demonstrate comprehensive understanding of web appliance capabilities, architectural components, and operational characteristics. This foundational knowledge provides the basis for all subsequent technical implementations and troubleshooting procedures.
Configuration management represents twenty percent of examination content, reflecting the critical importance of proper system setup and ongoing maintenance activities. Candidates must demonstrate proficiency in initial deployment procedures, system optimization techniques, and continuous configuration management practices ensuring optimal security posture and operational effectiveness.
Proxy services constitute ten percent of the examination, emphasizing implementation and management of proxy-based content filtering, traffic inspection, and policy enforcement mechanisms. This domain requires candidates to understand technical complexities of proxy operations and their integration within broader security architectures.
Authentication mechanisms account for ten percent of the assessment, highlighting the critical importance of identity verification and access control within web security implementations. Candidates must demonstrate expertise in various authentication protocols, integration methodologies, and best practices for maintaining secure access controls.
HTTPS decryption policies represent ten percent of examination content, focusing on complex technical and operational considerations involved in implementing encrypted traffic inspection capabilities. This domain requires understanding of certificate management, performance optimization, and privacy considerations associated with HTTPS inspection.
Traffic access policies constitute ten percent of the assessment, requiring candidates to demonstrate expertise in policy creation, implementation, and ongoing management activities. This includes understanding of rule prioritization, policy optimization, and troubleshooting techniques for complex policy implementations.
Acceptable use control mechanisms account for ten percent of the examination, focusing on implementation of content filtering, bandwidth management, and user behavior monitoring capabilities. Candidates must understand technical and operational aspects of implementing comprehensive acceptable use policies within enterprise environments.
Malware defense capabilities represent ten percent of the assessment, emphasizing the critical importance of threat detection, prevention, and response mechanisms within web appliance implementations. This domain requires understanding of various malware types, detection techniques, and response procedures.
Finally, reporting and tracking functionality constitutes ten percent of examination content, focusing on implementation and utilization of comprehensive monitoring and reporting capabilities enabling organizations to maintain visibility into their web security posture and compliance requirements.
Creating Effective Laboratory Environments for Hands-On Experience
The cornerstone of successful Cisco 300-725 SWSA certification preparation involves establishing realistic laboratory environments that enable authentic exploration of Cisco Web Security Appliance technologies. Candidates investing time in practical experimentation develop both technical familiarity and situational awareness needed to solve unexpected challenges during examinations and professional deployments.
Virtual laboratory implementations offer significant advantages for aspirants unable to access expensive physical hardware. Utilizing virtualization platforms, candidates can simulate web appliance environments that replicate enterprise configurations. These laboratory setups enable practice with routing, proxy services, HTTPS inspection, malware protection, and reporting capabilities without substantial financial investment. Through repeated configuration, troubleshooting, and repair of virtual instances, candidates develop instincts that become invaluable when encountering practical scenarios during examinations.
Comprehensive laboratory preparation should address every examination domain. This includes fundamental appliance installation, network integration, user authentication, acceptable use control, policy deployment, malware inspection, and system reporting. Each laboratory element should be interconnected, enabling candidates to observe how policy enforcement influences traffic flows, user access patterns, and security outcomes. When candidates experience the cause-and-effect relationships of policy modifications, theoretical concepts become deeply ingrained.
Exploring administrative interfaces and command-line tools enhances adaptability. The ability to navigate efficiently between GUI-based dashboards and command-line troubleshooting modes ensures fluency regardless of operational scenarios. Aspirants should experiment with diverse deployment models—explicit proxy, transparent proxy, and hybrid approaches—to understand flexibility across different environments.
Troubleshooting practice proves equally vital. Candidates should deliberately misconfigure policies, disrupt authentication flows, and simulate malware events to practice recovery strategies. Developing these reflexes enables them to remain calm under examination pressure and proficient in production environments where downtime directly impacts business continuity.
Maximizing Official Cisco Educational Resources
While practical laboratories develop skills, structured educational resources provide direction. Cisco's official educational ecosystem offers precise content aligned with examination objectives, making it the most reliable information source for the Cisco 300-725 SWSA certification.
The Cisco Learning Network serves as the cornerstone for candidates. It consolidates study resources including technical guides, whitepapers, frequently asked questions, and configuration manuals. Engaging with this platform exposes candidates to curated content and interactive community discussions where peers and experts exchange problem-solving strategies.
Instructor-led training courses enhance preparation by combining conceptual clarity with practical implementation exercises. Guided by experienced professionals, candidates can clarify nuanced topics such as authentication chain processing, HTTPS inspection tuning, and malware scanning integration. These sessions often simulate real deployment challenges, allowing aspirants to analyze scenarios similar to those presented during examinations.
For professionals with limited schedules, self-paced modules provide flexibility. These materials include digital handbooks, interactive laboratories, and video tutorials, enabling independent learners to progress steadily. Combining instructor-led learning with self-paced exploration ensures exposure to both structured frameworks and independent critical thinking.
Cisco's official examination guide remains indispensable. This roadmap lists domains, weightings, and competencies candidates must master. Reviewing it frequently ensures that preparation remains aligned with examination scope rather than drifting into tangential topics.
Implementing Effective Practice Testing Methodologies
Practice testing constitutes one of the most impactful preparation techniques for the Cisco 300-725 SWSA examination. It transforms knowledge into action by simulating examination conditions and highlighting both strengths and weaknesses.
Candidates should begin their journey with diagnostic assessments. These initial evaluations reveal which domains require deeper focus. For instance, a candidate may excel in malware defense but struggle with HTTPS inspection. Knowing this early allows targeted study instead of unfocused repetition.
As preparation progresses, candidates should increase practice test intensity. Timed simulations replicate the pressure of answering 55–65 questions within 90 minutes. Practicing under such conditions enhances pacing strategies, prevents overthinking, and builds familiarity with computer-based testing interfaces.
Detailed analysis of test results proves critical. Instead of merely noting scores, candidates must dissect incorrect answers to understand underlying misconceptions. This process transforms mistakes into learning opportunities and accelerates mastery. Maintaining a performance journal allows tracking improvement across weeks and reveals whether certain knowledge gaps persist.
Strategic repetition also builds resilience. By repeatedly encountering similar problem types, candidates recognize patterns in how Cisco designs questions. This pattern recognition accelerates comprehension and reduces hesitation during actual examinations.
Ultimately, practice testing functions as rehearsal not only for knowledge but also for confidence. It conditions candidates to remain composed and effective under examination-day stress.
Designing Structured Study Programs and Time Management Systems
Preparation without structure often results in wasted effort. Creating disciplined study plans tailored to the Cisco 300-725 SWSA certification ensures efficient time allocation across all domains.
The planning process begins with thorough review of the examination blueprint. Candidates must map out topics proportional to their weighting. For example, if traffic policies carry higher importance than reporting mechanisms, study time should be weighted accordingly.
Initial two to three weeks should focus on foundational principles. This includes appliance architecture, proxy modes, authentication options, and acceptable use policy fundamentals. Building this baseline knowledge equips candidates to handle advanced features with greater clarity.
Subsequent phases should concentrate on complex domains such as HTTPS inspection, malware scanning, and integration with external identity providers. These areas demand deeper technical focus and repeated laboratory practice to achieve fluency.
Time management strategies should prioritize daily consistency. Studying for shorter, focused intervals across several days yields better retention than sporadic marathon sessions. Allocating dedicated slots for laboratory practice, theory review, and practice testing ensures balanced development of all skills.
Incorporating buffer time proves vital. Unexpected delays, complex topics, or personal responsibilities may derail rigid schedules. Including contingency periods allows flexibility without sacrificing momentum.
Tracking progress through checklists, digital planners, or learning dashboards reinforces accountability. Visualizing milestones—such as completing a domain or improving a practice test score—provides motivation and clarity of direction.
Expanding Knowledge Through Advanced Technical Resources
While official Cisco resources and training form the backbone of preparation, ambitious candidates often extend their learning by exploring advanced technical references. These additional materials provide depth, context, and exposure to real-world scenarios that enrich examination preparation.
Whitepapers published by Cisco and other industry leaders delve into nuanced challenges such as encrypted traffic inspection, advanced malware analytics, and policy enforcement in hybrid cloud environments. Reading these documents enhances conceptual understanding beyond examination-specific requirements.
Case studies provide narratives of how enterprises deploy Cisco Web Security Appliances to counter evolving threats. Analyzing these case studies helps candidates contextualize abstract technical features into tangible business outcomes. This broader perspective improves reasoning when answering scenario-based examination questions.
Technical forums and professional communities also serve as valuable resources. Engaging with other practitioners exposes candidates to diverse troubleshooting approaches and unique implementation strategies. Such peer-to-peer learning offers perspectives rarely covered in structured training.
Additionally, experimenting with adjacent technologies enhances preparation. Understanding how web appliances integrate with firewalls, intrusion prevention systems, and identity platforms fosters a systems-level perspective. This holistic understanding often proves advantageous during simulation-style examination questions spanning multiple domains.
Ensuring Long-Term Knowledge Retention and Reinforcement
Sustainable success in the Cisco 300-725 SWSA examination requires more than short-term memorization. Candidates must adopt reinforcement strategies that ensure knowledge remains durable and accessible under examination pressure.
Spaced repetition represents one of the most effective techniques. Revisiting material at scheduled intervals strengthens memory encoding and prevents rapid forgetting. Candidates can use flashcards, digital platforms, or handwritten notes for periodic review.
Active recall further improves retention. Instead of rereading notes passively, candidates should test themselves by summarizing topics, answering mock questions, or teaching material to peers. The act of retrieving knowledge reinforces neural pathways more effectively than repetition alone.
Blending theoretical review with laboratory practice enhances both comprehension and recall. For instance, reading about HTTPS inspection policies should be immediately followed by implementing them in laboratory environments. This synthesis of knowledge and action makes recall more natural during examinations.
Documenting discoveries and troubleshooting steps during practice creates a personalized reference library. Reviewing this documentation before examinations consolidates learning and provides quick refreshers of complex tasks.
Peer discussions also contribute to retention. Explaining concepts to others forces candidates to articulate knowledge clearly, revealing any weaknesses requiring further study.
Advanced Proxy Service Implementation and Enterprise Traffic Control
Within the Cisco 300-725 SWSA certification context, advanced proxy services form the foundation of web appliance implementation. Beyond basic deployment, professionals must manage traffic flows with precision, ensuring enterprise networks maintain balance between security, performance, and end-user productivity.
Sophisticated proxy configurations must incorporate both explicit and transparent modes, with each offering specific benefits regarding control, visibility, and user transparency. Explicit proxy deployments, though more configurable, often require endpoint reconfiguration, while transparent proxying intercepts traffic seamlessly without modifying client devices. Candidates must know when to employ each approach, or combine them in hybrid architectures, to maximize operational efficiency.
Proxy chaining represents another complex concept frequently tested in advanced environments. In large-scale organizations with distributed traffic paths, chaining multiple proxies allows traffic redirection for layered inspection, redundancy, and specialized policy application. Understanding how to configure and optimize these chains while preventing bottlenecks proves crucial.
Equally important is the discipline of content categorization and filtering. Web appliances rely heavily on categorization databases and pattern matching algorithms to enforce browsing controls. Candidates must be able to fine-tune these systems, minimize false positives, and adapt filtering policies dynamically to evolving threats.
Load balancing introduces additional complexity. High-volume enterprises require distributed proxy clusters that provide resilience and efficiency. Designing active-active proxy architectures, implementing health monitoring, and fine-tuning failover procedures ensure continuous traffic inspection even during component outages. This mastery separates intermediate administrators from advanced professionals prepared for certification success.
Finally, integration of proxy services with authentication systems such as LDAP, Kerberos, or SAML ensures that security policies can be applied at granular user levels. For examinations, candidates must demonstrate familiarity with integrating proxies with external directories, implementing single sign-on, and troubleshooting protocol-level issues across distributed systems.
Advanced Authentication Integration and Enterprise Access Management
Modern enterprises demand authentication architectures that extend beyond traditional username and password combinations. Within the Cisco Web Security Appliance framework, authentication and access control must provide robust security while remaining seamless for users.
Candidates must demonstrate fluency in implementing multiple authentication protocols, including NTLM, Kerberos, and LDAP, ensuring interoperability with existing directory services. Integration with Active Directory or cloud-based identity services introduces challenges such as schema mapping, password policy enforcement, and synchronization accuracy.
Multi-factor authentication (MFA) becomes increasingly essential in enterprise-grade deployments. Professionals must integrate hardware tokens, SMS verification, certificates, or biometric systems into authentication workflows. A balanced approach proves necessary: while MFA strengthens defense against credential theft, poorly implemented systems can create usability barriers hindering adoption.
Role-based access control (RBAC) represents another complexity domain. Large organizations often maintain layered hierarchies where permissions differ not only by department but also by seniority, project assignment, or security clearance. Candidates must know how to configure inheritance models, dynamic access policies, and adaptive controls that adjust to context without overwhelming administrative teams.
Federated authentication introduces further challenges, especially when integrating with third-party services or external partners. Knowledge of SAML assertions, OAuth flows, and OpenID Connect ensures that web appliances can participate in identity federation without compromising trust boundaries.
Mastery of authentication also requires troubleshooting expertise. Failed logins, mismatched certificates, and expired tokens can all disrupt user experience and create administrative overhead. Being able to isolate and resolve such issues efficiently represents a core expectation of the 300-725 SWSA certification.
Advanced HTTPS Inspection and Certificate Authority Management
Encrypted traffic inspection represents one of the most demanding areas of web appliance management, both technically and ethically. With more than ninety percent of today's internet traffic encrypted, professionals must implement HTTPS inspection policies while maintaining compliance with privacy and regulatory frameworks.
The first mastery layer involves deep knowledge of cryptographic protocols including TLS 1.2, TLS 1.3, and associated cipher suites. Candidates must understand how these protocols establish secure channels, negotiate keys, and validate certificates. This foundation proves critical for configuring inspection without inadvertently weakening security.
Certificate management forms the backbone of HTTPS inspection. Implementing a trusted certificate authority within the web appliance allows it to perform man-in-the-middle inspection while maintaining user trust. Candidates must know how to generate, distribute, and manage CA certificates across enterprise endpoints without triggering browser warnings or application errors.
Selective inspection policies offer balance between visibility and privacy. Professionals must configure rules that bypass sensitive categories such as banking or healthcare while still inspecting suspicious or high-risk traffic categories. This requires nuanced policy design and awareness of compliance obligations such as GDPR or HIPAA.
Key management procedures further complicate operations. Generating secure keys, rotating them periodically, and storing them in hardware security modules ensures integrity against compromise. Examinations often evaluate knowledge of these processes, particularly how they integrate with enterprise key management solutions.
Certificate pinning introduces additional challenges, as applications enforcing strict certificate checks can break when inspected. Candidates must understand exception handling, revocation checking, and validation workflows to prevent legitimate traffic from being blocked while maintaining strong security.
Comprehensive Threat Protection and Intelligence Integration
In today's threat landscape, web appliances cannot rely solely on static filtering. Advanced malware defense requires layered strategies combining heuristic analysis, behavioral detection, and real-time threat intelligence feeds.
Candidates must demonstrate proficiency in configuring multi-layered defense mechanisms within Cisco Web Security Appliances. This includes integrating antivirus engines, enabling reputation-based filtering, and activating advanced features such as file sandboxing for dynamic malware analysis.
Sandboxing environments allow suspicious files to execute in isolated virtual environments where behavior can be analyzed without endangering production systems. Professionals must understand how to configure these environments, interpret sandbox reports, and automate response workflows.
Threat intelligence integration represents another core expectation. Web appliances must consume feeds from Cisco Talos or third-party sources, converting indicators of compromise into enforceable rules. Candidates must understand feed management, correlation analysis, and response automation.
Zero-day protection highlights modern defenses. Because unknown threats cannot be matched against signature databases, candidates must rely on heuristic techniques, anomaly detection, and machine learning-driven behavioral analysis. Implementing and fine-tuning these systems requires expertise in balancing detection accuracy with performance impact.
Integration with Security Information and Event Management platforms further expands visibility. By exporting logs, alerts, and threat events into centralized monitoring solutions, organizations can correlate events across multiple security systems. For certification, candidates must understand how to configure log exports, apply correlation rules, and develop coordinated response playbooks.
Implementing Policy Frameworks and Usage Governance
Beyond malware defense, enterprises must enforce acceptable use policies that align employee activity with organizational values, compliance requirements, and productivity goals. The Cisco 300-725 SWSA examination evaluates candidates' ability to implement these policies using advanced web filtering and governance tools.
Content categorization serves as a primary mechanism for enforcing acceptable use policies. Candidates must know how to configure category-based filtering rules, adjust sensitivity thresholds, and manage exceptions for business-critical websites.
Time-based controls provide flexibility by permitting or denying access to certain categories during specific hours. For instance, social media access might be blocked during work hours but allowed during breaks. Configuring these dynamic rules requires advanced policy design.
Bandwidth controls further extend governance by limiting access to high-bandwidth applications such as streaming video or file-sharing platforms. Professionals must demonstrate capability to apply shaping or throttling mechanisms without disrupting legitimate business traffic.
Policy reporting and user awareness mechanisms complement technical controls. Displaying customized block pages, generating usage reports, and integrating with HR compliance programs ensures transparency and accountability.
Finally, candidates must consider cultural and regional nuances when designing acceptable use policies. What constitutes acceptable use may vary between jurisdictions, and policies must respect legal frameworks while maintaining corporate standards. This strategic awareness proves as important as technical mastery.
Integration with Security Ecosystems and Cloud Infrastructure
Modern enterprises operate in hybrid environments where web appliances rarely function in isolation. The Cisco 300-725 SWSA certification therefore emphasizes integration with larger security ecosystems and cloud-based services.
Candidates must understand how to integrate appliances with firewalls, intrusion prevention systems, endpoint protection platforms, and cloud security gateways. Such integration ensures layered defense, reducing the chance of threat actors bypassing controls.
Cloud adoption introduces additional complexity. Professionals must master hybrid deployment strategies where web appliances coexist with cloud-based security services. This includes policy synchronization, unified reporting, and seamless user experience across on-premises and cloud inspection points.
Integration with identity services represents another key area. Synchronizing with cloud-based identity providers such as Azure AD or Okta ensures consistent policy enforcement regardless of user location. For remote workforces, this capability proves indispensable.
API-based integration expands automation potential. Candidates must understand how to leverage RESTful APIs for automating reporting, adjusting policies, and exporting telemetry to external monitoring platforms. This capability reflects the industry's shift toward programmability and automation-driven security management.
Advanced Data Management and Processing Frameworks
One of the defining challenges for professionals pursuing mastery in the Cisco 300-725 SWSA certification involves deploying robust data collection frameworks within web appliance ecosystems. Data serves as the foundation of security visibility, and without comprehensive capture methodologies, organizations risk blind spots that could leave them vulnerable to undetected threats.
Candidates must understand the intricacies of log aggregation at scale. In enterprise-grade environments, logs generate at extremely high velocities, with millions of entries recorded per second from proxies, authentication systems, policy engines, and malware inspection components. Configuring scalable pipelines that normalize this information without overwhelming storage systems requires proficiency in log transport protocols, parsing techniques, and deduplication strategies.
The sophistication of logging extends to careful balance between verbosity and practicality. Excessive logging can flood storage arrays and complicate analysis, whereas insufficient logging creates security gaps. Configuring correct log levels, ensuring rotation policies, and applying compression mechanisms ensures both retention and system stability.
Data enrichment enhances raw logs into actionable intelligence. Integrating feeds such as geolocation services allows administrators to identify suspicious activity based on region. Threat intelligence correlation provides context for flagged traffic, while categorization databases enhance visibility into user browsing patterns. Candidates must be adept at embedding these enrichment techniques directly into collection workflows to ensure downstream analytics operate on context-rich datasets.
Equally critical is real-time data processing. Modern organizations cannot rely solely on batch analysis; they require immediate visibility into anomalies. Stream processing frameworks, correlation engines, and inline policy enforcement mechanisms empower administrators to identify threats as they occur rather than hours later. For the Cisco 300-725 SWSA examination, understanding how to configure appliances for low-latency analytics proves essential for success.
Finally, data quality must not be underestimated. Professionals must implement error detection, validation workflows, and data consistency checks. Without these safeguards, analytic outputs risk being skewed by corrupted or incomplete data. Ensuring accuracy at the point of collection establishes a foundation for reliable insights across all subsequent reporting and compliance functions.
Comprehensive Analytics and Proactive Threat Intelligence
The analytics layer transforms raw data into actionable intelligence. Professionals pursuing certification must demonstrate advanced competency in applying statistical methodologies, anomaly detection techniques, and predictive modeling strategies that uncover both current risks and emerging trends.
User behavior analytics represents a major emphasis. By establishing baselines of expected browsing patterns, access times, and content categories, administrators can apply machine learning or heuristic algorithms to detect deviations. For example, an employee suddenly downloading gigabytes of data from unusual domains might trigger an alert for exfiltration risk. These capabilities rely on building reliable risk scoring frameworks, enabling prioritization of alerts.
Threat trend analysis provides another indispensable function. Using historical data combined with external intelligence feeds, administrators can identify which categories of attacks are rising in prevalence. This allows organizations to proactively adapt controls before attacks materialize at scale. For instance, a surge in credential-harvesting domains within specific regions may guide immediate implementation of stricter policy enforcement.
Performance analytics complements security metrics by ensuring that the web appliance infrastructure itself continues operating at scale. Administrators must define key performance indicators such as proxy latency, throughput efficiency, and connection drop ratios. By correlating security workloads with performance bottlenecks, professionals can preemptively scale capacity or adjust configurations to maintain resilience.
Custom analytics capabilities extend beyond pre-built dashboards. Professionals must craft bespoke queries, optimize database engines, and apply visualization frameworks that present highly contextual insights. Candidates preparing for the 300-725 SWSA examination must be familiar with building tailored dashboards, incorporating drill-down capabilities, and aligning visuals with both technical and executive-level stakeholders.
Advanced Compliance Management and Regulatory Reporting
Compliance has become inseparable from technical security operations, and mastery in regulatory reporting represents a central focus of advanced web appliance administration. Candidates must know how to design, implement, and automate reporting systems that demonstrate adherence to legal frameworks while supporting internal governance mandates.
Audit trail management forms the backbone of compliance. Administrators must guarantee log immutability, preventing tampering and ensuring chain-of-custody for forensic investigations. Configurations often involve write-once storage systems, cryptographic signing, and timestamp synchronization. These measures provide auditors with confidence in the authenticity of reported data.
Automated compliance monitoring reduces manual overhead by continuously validating system configurations against policy baselines. Professionals must implement detection rules that immediately highlight deviations, exceptions, or unauthorized modifications. Automated remediation tracking further ensures that once violations are detected, corrective action is documented and followed through.
Data retention policies often present complex challenges. Regulatory bodies mandate retention periods ranging from months to years depending on industry. Administrators must configure retention schedules, secure archival systems, and develop retrieval mechanisms that allow rapid access during audits. Simultaneously, storage optimization and encryption safeguards must protect sensitive historical data from misuse.
Privacy protections demand another layer of expertise. Organizations must enforce anonymization techniques that strip personally identifiable information while retaining analytic value. Access control lists, encrypted storage, and audit mechanisms ensure that sensitive logs are available only to authorized individuals. For candidates, demonstrating knowledge of these practices proves crucial, as mishandling privacy often results in severe legal consequences.
Executive reporting introduces unique communication challenges. Leaders and board members require concise summaries of compliance status without being overwhelmed by technical minutiae. Professionals must aggregate key statistics, apply visualization techniques, and communicate findings in terms of risk reduction, business continuity, and regulatory exposure. Developing these executive dashboards involves as much storytelling as technical precision.
Enterprise Security Ecosystem Integration
Web appliances do not operate in isolation; they form one component of multilayered defense strategies. For this reason, the Cisco 300-725 SWSA certification emphasizes proficiency in integration with broader enterprise ecosystems, including SIEM platforms, incident response frameworks, and threat intelligence communities.
SIEM integration often represents the first step. By exporting logs and alerts into centralized systems, administrators enable correlation with data from firewalls, intrusion prevention systems, and endpoint agents. Candidates must know how to configure log forwarding, normalize formats, and apply correlation rules that uncover sophisticated attack campaigns spanning multiple vectors.
Orchestration technologies extend integration further by enabling automated workflows. When a web appliance detects malware, an orchestration platform can automatically quarantine affected endpoints, update firewalls, and notify incident response teams. Understanding workflow automation design, playbook development, and integration protocols proves critical for certification.
Threat intelligence sharing also plays a key role. Web appliances must be capable of consuming standardized formats such as STIX and TAXII, while also sharing anonymized insights with community partners. Proper implementation requires balancing collaboration benefits with the need to safeguard organizational confidentiality.
Custom integrations often rely on application programming interfaces. Candidates must demonstrate the ability to leverage RESTful APIs for exporting data, triggering external actions, or integrating with cloud-native monitoring tools. Error handling, rate limiting, and authentication models must all be considered when designing these integrations.
Building Predictive Security Models Through Advanced Analytics
Moving beyond compliance and integration, advanced professionals employ analytics for predictive security. This involves combining machine learning algorithms, statistical modeling, and historical data to forecast likely attack vectors and capacity requirements.
Predictive traffic modeling allows organizations to anticipate surges in specific categories, enabling proactive resource allocation. For example, anticipating spikes in streaming services during global events helps administrators balance acceptable use controls with bandwidth preservation.
Threat forecasting leverages external intelligence feeds and historical correlation to predict which industries or geographies may become targets of emerging campaigns. This allows security teams to harden defenses in advance rather than reacting after breaches occur.
Capacity planning benefits significantly from predictive modeling as well. By correlating user behavior with seasonal or organizational trends, professionals can ensure sufficient proxy and inspection resources during peak demand cycles.
Candidates preparing for certification must understand both the technical implementation of predictive models and the organizational implications of acting upon predictions. Predictions must be contextualized, validated, and communicated effectively to leadership before resource investments are made.
Enhanced Visualization and Strategic Communication
The complexity of analytics and compliance data requires clear, actionable communication. Visualization extends beyond aesthetics; it determines whether technical insights influence strategic decisions.
Professionals must master dashboard design that combines clarity with depth. Interactive elements such as drill-downs allow executives to explore specific incidents while retaining high-level overviews. Visualization frameworks must incorporate color coding, risk scoring, and temporal trends to highlight both urgency and long-term trajectories.
Storytelling proves equally important. Executives rarely need packet-level detail; they require narratives that tie technical incidents to business impact. Professionals must translate metrics such as proxy hit ratios or TLS handshake failures into implications for productivity, legal exposure, or brand reputation.
Regular reporting cycles, whether monthly compliance summaries or real-time security dashboards, ensure that decision-makers remain informed. Automated delivery mechanisms streamline this process, ensuring consistency and timeliness without manual intervention.
For examinations, candidates must demonstrate familiarity with both the technical configuration of visualization systems and the communication strategies required to translate insights effectively across diverse audiences.
Strategic Career Positioning and Professional Differentiation
In today's cybersecurity landscape, organizations face escalating threats and increasingly complex regulatory demands. Against this backdrop, professionals with specialized skills in web appliance security stand out markedly. The Cisco 300‑725 SWSA certification signals mastery of web security technologies and alarm management on Cisco Secure Web Appliance platforms, establishing a distinct professional identity. This differentiation is crucial in a competitive marketplace, particularly when organizations seek talent capable of delivering immediate, high‑impact contributions without protracted onboarding.
Certified professionals can credibly position themselves as indispensable assets within web security teams, offering refined technical acumen in appliance configuration, policy enforcement, threat detection, and incident mitigation. This perceived readiness enhances career mobility, strengthens negotiating positions for higher compensation, and generates institutional trust. Moreover, the restricted supply of deeply skilled SWSA experts induces a scarcity premium—employers are often willing to offer accelerated advancement paths, leadership roles, and compensation packages that reflect the unique proficiency such professionals bring to organizational cybersecurity resilience.
Direct Career Avenues: Web Security Administrator and Analyst
One of the most natural vocational trajectories for Cisco 300‑725 SWSA credential holders is in roles such as Web Security Administrator or Analyst. These positions focus squarely on operating and optimizing Secure Web Appliance frameworks. Responsibilities typically include crafting granular security policies, monitoring traffic flows for threats like malware, phishing, or data leakage, and tuning appliance configurations to balance security efficacy with user productivity.
These roles cultivate technical depth and strategic influence—analysts often act as first responders to security incidents, conducting forensic reviews, implementing real-time protection rules, and refining policy sets based on emerging patterns. Over time, professionals in these roles become trusted guardians of web perimeter security, gaining visibility among IT leadership and influencing broader cybersecurity strategy.
Broader Security Architect and Network Engineering Roles
Certified experts in Cisco web security technologies often advance into broader roles like Network Security Engineer or Security Architect. Such positions demand holistic understanding of enterprise security architectures—spanning firewalls, intrusion prevention, email and web gateways, VPN systems, and secure access frameworks.
Professionals merge their appliance-specific expertise with wider network security knowledge to design integrated defense architectures. Cross-functional design capabilities—for instance, integrating web appliances with threat intelligence feeds, SIEM systems, or endpoint protection platforms—highlight their strategic value. In these roles, certified professionals drive secure enterprise transformation, define best practices, and ensure that web traffic protection dovetails seamlessly with organizational policy and infrastructure.
Consulting and Professional Services Pursuits
For certified professionals seeking dynamic and varied career experiences, roles in Cybersecurity Consulting or Professional Services represent excellent opportunities. In these capacities, professionals apply their web appliance specialization across diverse client environments—tailoring deployments, performing readiness assessments, and optimizing policy architectures.
Consultants must navigate heterogeneous landscapes—adjusting appliance settings to meet clients’ regulatory obligations, business workflows, and network topologies. This breadth of exposure rapidly accelerates their skill maturity while honing soft skills such as client communication, risk analysis, and solution design. Consulting roles often yield elevated compensation, flexibility, and accelerated promotion pathways due to their breadth and complexity.
Vendor- and Integrator-Based Specialist Roles
Cisco Security Specialist roles housed within vendors, system integrators, or channel partners offer another key advancement avenue. Here, professionals serve both as technical subject-matter experts and as customer-facing educators—supporting appliance deployment, delivering training, and influencing product development by relaying field feedback.
These positions provide a strategic vantage point—certified professionals refine best practices, contribute to technical documentation, and shape appliance enhancements alongside engineering teams. This dual domain of customer engagement and product immersion accelerates professional development while amplifying impact across the vendor ecosystem.
Operational Security Engineering: The Vigilant Backbone of Web Defense
Operational Security Engineering encompasses the day-to‑day governance of web security systems, demanding professionals who relish hyper‑vigilant, real‑time environments. These roles pivot around ceaseless monitoring, early detection, and proactive fortification of digital infrastructures. Engineers assume the mantle of guardians, scrutinizing traffic flows, discerning anomalies, calibrating rulesets, and sustaining resilience across the networked terrain. The remit extends from parsing voluminous log streams to nurturing the operational integrity of security appliances, ensuring they remain robust and responsive against nefarious incursions.
Such roles are not merely mechanistic—they engage one’s analytical faculties, pattern recognition, and ability to discern subtle threat vectors. Effective engineers curate adaptive filtering policies, tailoring defenses in accordance with evolving threat landscapes. They leverage SWSA‑level acuity to understand attack surfaces and deploy defense mechanisms with granular precision. This dynamic interplay between human insight and automated safeguards fosters a proactive posture, where vulnerabilities are preemptively mitigated rather than remediated post‑breach.
Operational Security Engineering positions thus offer more than just repetitive tasks—they cultivate cyber‑sagacity. Daily interaction with alerts, dashboards, and appliance telemetry fine‑tunes one’s intuition. Over time, seasoned practitioners evolve into custodians of network sanctity, ever ready to pivot when anomalies emerge. The role’s ceaseless flux erodes complacency, sharpening reflexes and engendering a mindset attuned to detecting the subtlest existential threats.
Incident Response Workflows: From Detection to Remediation
Within the ambit of IT Security Operations Engineering, incident response is a pulsating, mission‑critical dimension. At its core lies a structured workflow that begins with detection—the moment anomalous activity is flagged via behavioral deviations, signature hits, or heuristic triggers. Engineers spring into action, triaging alerts to discern false positives from authentic incidents. Rapid situational awareness is paramount: Is the anomaly localized or pervasive? What systems, users, or endpoints are implicated?
Once the initial alert is validated, containment measures are swiftly enacted. Engineers isolate compromised endpoints—segregating devices from the network to forestall lateral propagation of threats. They revoke conspicuous or compromised user access, erecting temporary barriers while preserving forensic integrity. Throughout this process, logs are harvested and snapshots taken, enabling retrospective analysis.
Subsequently, remediation strategies emerge: patches and updates are applied, misconfigurations remediated, and policies refined. Engineers recalibrate threat filters, enhance signatures, and adjust anomaly thresholds to reinforce resilience. Analytical reports distilled from threat intelligence inform these changes, ensuring defenses incrementally evolve in step with adversary ingenuity.
Post‑incident, a retrospective review—sometimes called a post‑mortem—identifies root causes, gaps, and process improvements. This cyclical feedback loop strengthens future readiness, while documentation enhances organizational memory. Engineers emerging from these crucibles gain profound insights into attacker modus operandi, forensic techniques, and threat coherence.
Daily Governance of Security Infrastructure
Monitoring traffic patterns constitutes the daily heartbeat of Operational Security Engineering. Engineers scrutinize flow data, transaction volumes, geolocation anomalies, and protocol deviations. They cultivate baselines—normative traffic signatures against which aberrations stand out. Whether it’s a burst of encrypted traffic from an unrecognized region or repeated failed authentications, these nuances are detected early and investigated swiftly.
Security appliances—web application firewalls, intrusion prevention systems, proxy gateways, and load balancers—must operate with unerring uptime. Engineers monitor health metrics, ensure high‑availability clusters remain in sync, and perform failover drills. Firmware updates, patch application, and configuration backups are scheduled carefully to avoid disruptions, reflecting meticulous planning and orchestration.
Policy fine‑tuning is a continual endeavor. Engineers craft and refine granular rules: rate‑limiting, geofencing, content‑sanitization, bot‑mitigation, and session integrity checks. These policies evolve in response to emergent attack vectors such as credential stuffing, evasive malware, or API abuse. The capability to sculpt precision‑targeted filter logic without collateral disruption is a hallmark of adept practitioners.
Skill Enrichment Through Real‑Time Threat Exposure
Repeated immersion in emergent threat dynamics and appliance behaviors engenders rare expertise. Engineers recognize early signs of DNS‑based infiltration, subtle TLS renegotiation anomalies, or lateral reconnaissance by sophisticated threat actors. This empirical acumen surpasses textbook learning, embedding tacit knowledge that’s difficult to replicate.
With each alert, false positive, and enriched signature set, engineers internalize the interplay between benign anomalies and malicious behavior. They sharpen their deductive reasoning, espouse a strategic mindset, and cultivate instincts oriented toward safeguarding ecosystem continuity. The role becomes less about command‑and‑control and more about becoming a sentinel—an instinctual defier of threats.
Foundations of Security Leadership: From Technician to Strategist
In the complex digital battlefield where adversaries evolve rapidly and organizations face continuous onslaughts, the role of the Operational Security Engineer transcends basic infrastructure management. These individuals are the vanguard of cyber resilience—handling security tooling, incident triage, infrastructure monitoring, and policy enforcement with surgical precision. Yet for many, the technical expertise gained from this hands-on vigilance is only the beginning. Transitioning into leadership roles such as Incident Response Manager or SOC lead requires a multifaceted evolution—intellectual, strategic, and interpersonal.
To make this progression, engineers must begin translating tactical experience into broader strategic vision. The journey from reactive defense to proactive orchestration is gradual but essential. Engineers need to understand not just how systems operate under stress, but also how people, processes, and technologies must harmonize during security crises. The unique exposure operational engineers receive to real-world incidents grants them a foundation that, when properly cultivated, elevates them into indispensable leaders.
This transformation requires more than technical mastery—it demands emotional intelligence, structured communication, risk comprehension, and cross-functional coordination. Leadership in cybersecurity is no longer about who understands logs the best, but who can decode them into actionable intelligence and rally teams around mitigation and learning.
Strategic Vision: The Transition from Response to Anticipation
Becoming a leader in cybersecurity incident response necessitates a refined sense of anticipation. Operational Security Engineers, often entrenched in detection and response, learn to recognize patterns—malicious behaviors that seem innocuous until viewed at scale or in retrospect. Leaders, however, must apply this same perception to organizational readiness.
A shift must occur from task-level execution to outcome-oriented strategy. Instead of just containing threats, future incident response managers must assess organizational posture, identify systemic weaknesses, and lead cross-functional initiatives to improve threat resilience. This means overseeing everything from threat modeling and tabletop exercises to red-team simulations and response rehearsals.
Such leaders operate with a mental map of the entire organization’s digital ecosystem. They visualize attack surfaces, map data flows, understand third-party risks, and quantify potential impact. Their vision extends beyond firewalls and signatures; it encompasses vendor dependency chains, remote access vulnerabilities, behavioral anomalies, and business continuity implications.
This strategic foresight separates leaders from technologists. While engineers focus on eradication and recovery, leaders build the framework that ensures future incidents are less likely or less damaging. It’s the difference between firefighting and fireproofing.
Cross-Functional Collaboration: The Language of Leadership
Technical acumen alone cannot elevate an engineer into a leadership role. True leadership in the realm of incident response is rooted in communication. The ability to speak fluently with disparate teams—legal, compliance, public relations, executive leadership, human resources—is non-negotiable. During critical incidents, these departments converge with varying concerns: brand reputation, regulatory exposure, legal liability, and customer trust. An incident response leader must be the linchpin, bridging gaps and translating cyber risk into understandable, actionable language.
Operational engineers already have a tactical understanding of alert validation, log correlation, and endpoint containment. Leadership, however, requires narrative construction. Leaders articulate what happened, how it happened, the impact, and the next steps—often to non-technical audiences under intense pressure.
Effective incident response managers exhibit clarity under duress. They maintain coherence when timelines compress and reputations hang in the balance. They do not simply escalate issues; they manage expectations, define priorities, and direct coordinated responses. Their interpersonal fluency becomes their superpower—commanding credibility and trust across the entire organization.
Cross-functional collaboration also extends to external parties—government entities, industry consortia, forensic vendors, and intelligence sharing alliances. A successful leader curates these relationships in advance, knowing that during a breach, established trust accelerates cooperation and minimizes chaos.
Tactical Mastery to Strategic Dexterity: Leveraging Hands-On Experience
One of the key differentiators between promoted engineers and stagnant ones is how effectively they convert their hands-on experience into strategic capabilities. Years of monitoring traffic, analyzing attack chains, and tuning SIEM rules cultivate a unique muscle memory. However, without reflection and contextualization, such experience remains tactical.
Future SOC leaders must extract lessons from daily engagements—documenting threat patterns, building playbooks, codifying incident timelines, and identifying operational inefficiencies. By contributing to institutional memory, engineers begin to see their knowledge not as isolated fixes but as frameworks for resilience. They move from being a solver of incidents to an architect of defenses.
Consider the nuance in an engineer who recognizes that repeated phishing-related escalations point not just to attacker ingenuity, but to insufficient user training or flawed mail filtering logic. Such a mindset initiates broader campaigns: user awareness drives, policy revisions, and technology reconfigurations. These strategic actions reflect leadership potential and business alignment.
Moreover, engineers seeking leadership must develop dexterity in metrics. Decision-makers prioritize data-driven reports: mean time to detect (MTTD), mean time to respond (MTTR), volume of false positives, root cause recurrence, and impact quantification. Future leaders must wield these indicators to assess SOC performance, drive improvement, and justify investments.
Situational Command: Crisis Management and Real-Time Decision-Making
No path to security leadership is complete without mastery of incident command. Crises are crucibles where potential leaders are forged—or exposed. The suddenness of a ransomware detonation, a zero-day exploit in active use, or the exfiltration of customer data requires composed, confident, and clear-headed direction. This is where years of technical experience must blend with strategic agility.
A capable incident response manager must assess impact within minutes, marshal the right stakeholders, and control the tempo of communication both internally and externally. Decisions must be made without perfect information—quarantining hosts, revoking credentials, taking systems offline, notifying authorities—all while managing legal obligations and customer expectations.
Operational engineers who aspire to leadership must cultivate this decision-making capacity. They must embrace ambiguity, balance technical and business risks, and act swiftly yet judiciously. Training through simulations, retrospectives, and tabletop exercises reinforces these capabilities.
The situational command also includes emotional regulation. Engineers unaccustomed to executive scrutiny may falter under pressure. Leaders, by contrast, must embody calm authority—projecting confidence, aligning teams, and ensuring that chaos remains outside the command room, not within.
Cisco SWSA 300-725 practice test questions and answers, training course, study guide are uploaded in ETE Files format by real users. Study and Pass 300-725 Securing the Web with Cisco Web Security Appliance (300-725 SWSA) certification exam dumps & practice test questions and answers are to help students.
- 200-301 - Cisco Certified Network Associate (CCNA)
- 350-401 - Implementing Cisco Enterprise Network Core Technologies (ENCOR)
- 350-701 - Implementing and Operating Cisco Security Core Technologies
- 300-410 - Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)
- 300-715 - Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)
- 350-801 - Implementing Cisco Collaboration Core Technologies (CLCOR)
- 350-601 - Implementing and Operating Cisco Data Center Core Technologies (DCCOR)
- 300-420 - Designing Cisco Enterprise Networks (ENSLD)
- 300-425 - Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)
- 300-415 - Implementing Cisco SD-WAN Solutions (ENSDWI)
- 300-710 - Securing Networks with Cisco Firewalls
- 200-901 - DevNet Associate (DEVASC)
- 820-605 - Cisco Customer Success Manager (CSM)
- 300-620 - Implementing Cisco Application Centric Infrastructure (DCACI)
- 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- 350-901 - Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
- 350-501 - Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)
- 400-007 - Cisco Certified Design Expert
- 300-730 - Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)
- 300-430 - Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)
- 500-220 - Cisco Meraki Solutions Specialist
- 300-435 - Automating Cisco Enterprise Solutions (ENAUTO)
- 350-201 - Performing CyberOps Using Core Security Technologies (CBRCOR)
- 300-810 - Implementing Cisco Collaboration Applications (CLICA)
- 100-150 - Cisco Certified Support Technician (CCST) Networking
- 300-820 - Implementing Cisco Collaboration Cloud and Edge Solutions
- 300-735 - Automating Cisco Security Solutions (SAUTO)
- 700-805 - Cisco Renewals Manager (CRM)
- 300-815 - Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)
- 300-610 - Designing Cisco Data Center Infrastructure for Traditional and AI Workloads
- 300-745 - Designing Cisco Security Infrastructure
- 300-440 - Designing and Implementing Cloud Connectivity (ENCC)
- 300-510 - Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)
- 300-720 - Securing Email with Cisco Email Security Appliance (300-720 SESA)
- 300-835 - Automating Cisco Collaboration Solutions (CLAUTO)
- 300-910 - Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)
- 500-442 - Administering Cisco Contact Center Enterprise
- 700-250 - Cisco Small and Medium Business Sales
- 300-725 - Securing the Web with Cisco Web Security Appliance (300-725 SWSA)
- 300-215 - Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
- 300-445 - Designing and Implementing Enterprise Network Assurance
- 300-635 - Automating Cisco Data Center Solutions (DCAUTO)
- 100-140 - Cisco Certified Support Technician (CCST) IT Support
- 300-615 - Troubleshooting Cisco Data Center Infrastructure (DCIT)
- 300-630 - Implementing Cisco Application Centric Infrastructure - Advanced
- 500-560 - Cisco Networking: On-Premise and Cloud Solutions (OCSE)
- 500-444 - Cisco Contact Center Enterprise Implementation and Troubleshooting (CCEIT)
- 300-515 - Implementing Cisco Service Provider VPN Services (SPVI)
- 700-750 - Cisco Small and Medium Business Engineer
- 700-240 - Cisco Environmental Sustainability Overview
- 700-245 - Environmental Sustainability Practice-Building
- 700-150 - Introduction to Cisco Sales (ICS)
- 800-150 - Supporting Cisco Devices for Field Technicians
- 100-490 - Cisco Certified Technician Routing & Switching (RSTECH)
Why customers love us?
What do our customers say?
The resources provided for the Cisco certification exam were exceptional. The exam dumps and video courses offered clear and concise explanations of each topic. I felt thoroughly prepared for the 300-725 test and passed with ease.
Studying for the Cisco certification exam was a breeze with the comprehensive materials from this site. The detailed study guides and accurate exam dumps helped me understand every concept. I aced the 300-725 exam on my first try!
I was impressed with the quality of the 300-725 preparation materials for the Cisco certification exam. The video courses were engaging, and the study guides covered all the essential topics. These resources made a significant difference in my study routine and overall performance. I went into the exam feeling confident and well-prepared.
The 300-725 materials for the Cisco certification exam were invaluable. They provided detailed, concise explanations for each topic, helping me grasp the entire syllabus. After studying with these resources, I was able to tackle the final test questions confidently and successfully.
Thanks to the comprehensive study guides and video courses, I aced the 300-725 exam. The exam dumps were spot on and helped me understand the types of questions to expect. The certification exam was much less intimidating thanks to their excellent prep materials. So, I highly recommend their services for anyone preparing for this certification exam.
Achieving my Cisco certification was a seamless experience. The detailed study guide and practice questions ensured I was fully prepared for 300-725. The customer support was responsive and helpful throughout my journey. Highly recommend their services for anyone preparing for their certification test.
I couldn't be happier with my certification results! The study materials were comprehensive and easy to understand, making my preparation for the 300-725 stress-free. Using these resources, I was able to pass my exam on the first attempt. They are a must-have for anyone serious about advancing their career.
The practice exams were incredibly helpful in familiarizing me with the actual test format. I felt confident and well-prepared going into my 300-725 certification exam. The support and guidance provided were top-notch. I couldn't have obtained my Cisco certification without these amazing tools!
The materials provided for the 300-725 were comprehensive and very well-structured. The practice tests were particularly useful in building my confidence and understanding the exam format. After using these materials, I felt well-prepared and was able to solve all the questions on the final test with ease. Passing the certification exam was a huge relief! I feel much more competent in my role. Thank you!
The certification prep was excellent. The content was up-to-date and aligned perfectly with the exam requirements. I appreciated the clear explanations and real-world examples that made complex topics easier to grasp. I passed 300-725 successfully. It was a game-changer for my career in IT!